In my last two blogs, I delved into the results of the 2025 Cisco Segmentation Report to highlight the importance of macro- and micro-segmentation and to identify the primary challenges hindering segmentation journeys. Today, I dive further into the survey results to discuss the benefits organizations can achieve when they successfully implement a dual macro- and micro-approach to segmentation. The goal, of course, is to continue highlighting insights into the current state of this critical cybersecurity concept and where it may be headed in the future.
Three Benefits of a Successful Segmentation Strategy
The good news is that the survey results indicate that organizations further along in their segmentation journeys are indeed achieving measurable benefits from their successful macro- and micro-segmentation implementations.
1. Contain Breaches
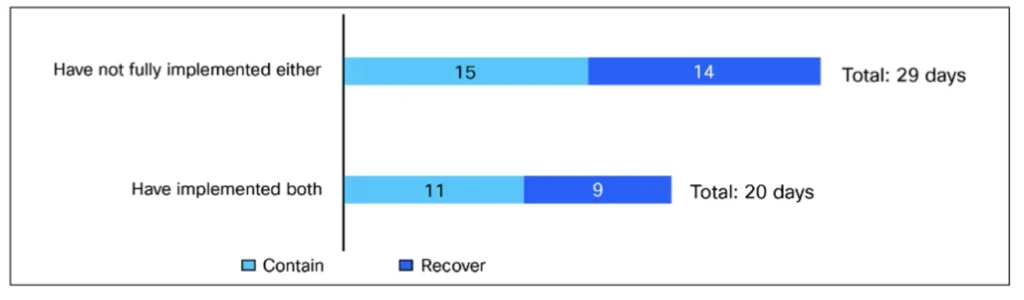
We all know that it’s not a matter of if your organization will get breached, it’s a matter of when. And, when it happens, you’ll need to detect the attack, identify its targets, understand the impact, contain the breach, and get systems back up and running as quickly as possible. Implementing both macro- and micro-segmentation enables faster breach response by providing organizations with pre-made defensive barriers. The survey responses support this. Respondents from organizations that have fully implemented macro- and micro-segmentation say that breach containment and recovery time take up to 20 days on average, compared with the reported 29 days for organizations without full implementation of both. This 31% faster recovery time is a real, measurable impact of a dual macro- and micro-segmentation approach. It is not hard to imagine how the reduction in containment and recovery comes about—after all, segmentation impedes attackers, thereby reducing the post-breach effort.

2. Protect High-Value Assets
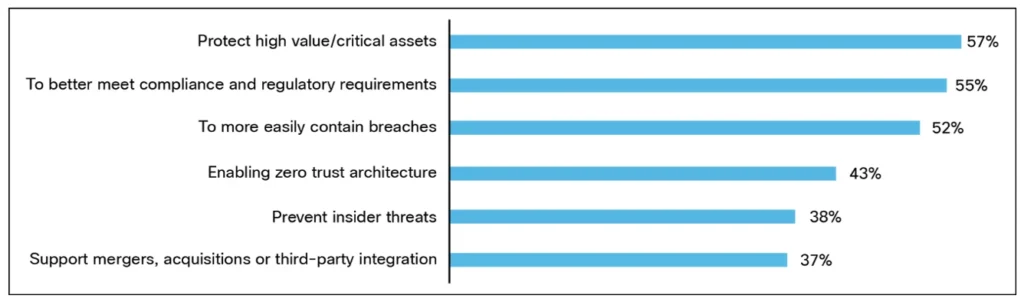
According to the report, protecting high-value/critical assets (57%) is the most likely driver for organizations implementing segmentation, including sensitive data, applications, and systems that are critical for business operations and continuity. On its face, protecting critical assets is useful, but preventing these assets from falling into the hands of threat actors preserves the organization’s reputation among customers, employees, shareholders, and other stakeholders. For example, an organization’s financial information can be protected by deploying segmentation that takes into account the identity of users. With such segmentation, only employees in the finance group are allowed access to finance applications. While this type of segmentation doesn’t prevent all kinds of attacks, it does raise the barrier to successful attacks.

3. Meet Compliance Requirements
Once the fundamentals of asset protection are in place, mature organizations extend segmentation into compliance-driven areas. This reflects both regulatory demands—in some major industry segments, such as retail, healthcare, and finance, organizations’ viability depends on their adherence to compliance standards, including PCI-DSS, HIPAA, and SOX (respectively)—and the pursuit of more comprehensive control across complex environments. The survey report shows that organizations with full segmentation deployment are more likely (67% vs 54%) to have also segmented workloads with compliance requirements.
Acknowledging the Impact of Segmentation
Organizations that have fully implemented a dual approach to segmentation (33% of respondents) can point to measurable impact—including better breach containment, asset protection, and higher focus on compliance. Clearly, these are adequate incentives for the remaining organizations (67% of respondents) that do not yet have full segmentation deployments to take action.
If you haven’t already, check out the first two blogs in the series, which discuss the importance of segmentation and the challenges organizations face when implementing segmentation projects. In the meantime, download the 2025 Cisco Segmentation Report to learn more about the state of segmentation today and where you fit against similar organizations.
We’d love to hear what you think! Ask a question and stay connected with Cisco Security on social media.
Cisco Security Social Media

