
A new Android spyware called ClayRat is luring potential victims by posing as popular apps and services like WhatsApp, Google Photos, TikTok, and YouTube.
The malware is targeting Russian users through Telegram channels and malicious websites that appear legitimate. It can steal SMS meessages call logs, notifications, take pictures, and even make phone calls.
Malware researchers at mobile security company Zimperium say that they documented more than 600 samples and 50 distinct droppers over the past three months, indicating an active effort from the attacker to amplify the operation.
ClayRat campaign
The ClayRat campaign, named after the malware’s command and control (C2) server, uses carefully crafted phishing portals and registered domains that closely mimic legitimate service pages.
These sites host or redirect visitors to Telegram channels where the Android package files (APKs) are provided to unsuspecting victims.
To add legitimacy to these sites, the threat actors have added fake comments, inflated download counts, and used a bogus Play Store-like UX with step-by-step instructions on how to sideload APKs and bypass Android’s security warnings.
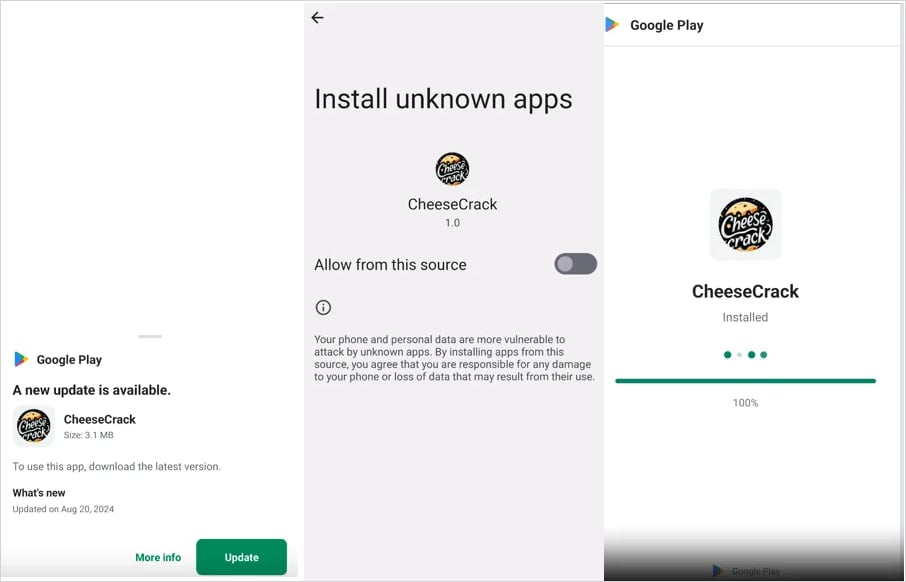
Source: Zimperium
According to Zimperium, some ClayRat malware samples act as droppers, where the app the user sees is a fake Play Store update screen and an encrypted payload is hidden in the app’s assets.
The malware nests in the device using a “session-based” installation method to bypass Android 13+ restrictions and reduce user suspicion.
“This session-based installation method lowers perceived risk and increases the likelihood that a webpage visit will result in spyware being installed,” the researchers say.
Once active on the device, the malware can use the new host to propagate to more victims by using it as a springboard to send SMS to the victim’s contact list.
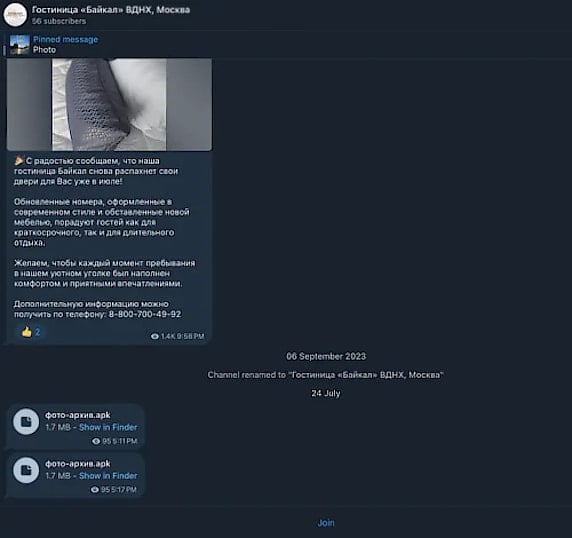
Source: Zimperium
Spyware’s capabilities
The ClayRat spyware assumes the default SMS handler role on infected devices, allowing it to read all incoming and stored SMS, intercept them before other apps, and modify SMS databases.
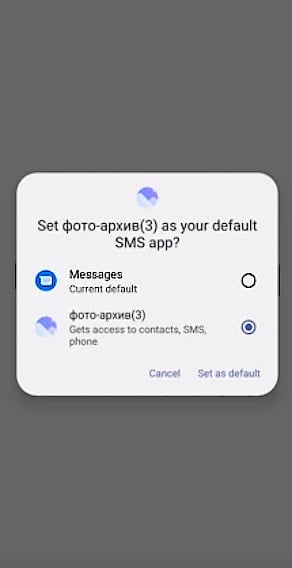
Source: Zimperium
The spyware establishes communication with the C2, that are AES-GCM encrypted in its latest versions, and then receives one of the 12 supported commands:
- get_apps_list — send list of installed apps to C2
- get_calls — send call logs
- get_camera — take a front-camera photo and send it to the server
- get_sms_list — exfiltrate SMS messages
- messsms — send mass SMS to all contacts
- send_sms / make_call — send SMS or place calls from the device
- notifications / get_push_notifications — capture notifications and push data
- get_device_info — collect device information
- get_proxy_data — fetch a proxy WebSocket URL, append device ID, and initialize a connection object (converts HTTP/HTTPS to WebSocket and schedules tasks)
- retransmishion — resend an SMS to a number received from C2
When the required permissions are granted, the spyware automatically harvests contacts and programmatically composes and sends SMS messages to every contact for en-masse propagation.
As a member of the App Defense Alliance, Zimperium shared the full IoCs with Google, and Play Protect now blocks known and new variants of the ClayRat spyware.
However, the researchers uunderline that the campaign is massive, with more than 600 samples on record in three months.


