“How could they see anything but the shadows if they were never allowed to move their heads?” — Plato, The Republic, Book VII
Introduction: The Shadows of Governance
In the allegory of Plato’s Cave, prisoners are chained in darkness, mistaking shadows cast on a wall for reality. Only by breaking free can they discover the truth outside the cave. Modern organizations face a similar challenge particularly in cybersecurity governance and enterprise digital transformation. The shadows in this digital cave are rigid hierarchies, performative compliance, fear-based leadership, and change resistance. These distort the truth, sabotage risk management, and create false security postures. This blog explores the “dark side” of cybersecurity governance using Plato’s Cave as a metaphor, showing how these hidden forces harm organizations, and how Cybersecurity Warrior Leaders (CWLs) can help lead them out of the cave and into governance transformation and maturity.
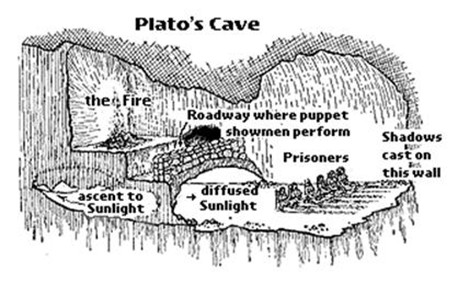
From Great Dialogues of Plato (Warmington and Rouse, eds.) New York, Signet Classics: 1999. p. 316.
Cybersecurity Governance
Cybersecurity governance refers to the structures, policies, and processes that ensure an organization’s information security strategy supports its business objectives, complies with regulations, and manages risk effectively (NIST, 2024). In modern digital enterprises, governance must evolve from static, compliance-driven models to adaptive, risk-informed approaches aligned with technological disruption, evolving global threats, and strategic agility. A digital enterprise is an organization that uses digital technologies not just to enhance operations but to transform business models, value delivery, and decision-making (Kane et al., 2015). These enterprises operate in real-time, treat data as a strategic asset, and integrate digital strategy into culture, people, and processes. Unlike traditional enterprises, which rely on static processes, top-down control, and legacy systems, digital enterprises function as complex adaptive ecosystems. These operational changes profoundly affect cybersecurity governance. The traditional, siloed model gives way to intelligence-driven, risk-aligned, and integrated approaches. As a result, leadership must evolve from command-and-control to Cybersecurity Warrior Leaders (CWLs) who embody digital fluency, emotional intelligence, and cyber risk-informed decision-making.
Digital Enterprise Change
Digital enterprise change involves the deep and continuous transformation of an organization’s leadership, culture, capabilities, and operating model through the strategic integration of digital technologies. It is not limited to adopting new tools or platforms but encompasses how the organization evolves its decision-making, collaboration models, and customer engagement in response to fast-moving digital ecosystems (Kane et al., 2015). Change must be proactive, iterative, and inclusive of all levels of the organization. This transformation impacts cybersecurity governance significantly. As digital enterprises become more complex and interconnected, traditional siloed approaches to cybersecurity governance prove inadequate. Success requires agile, cross-functional governance models capable of integrating cybersecurity into every stage of digital transformation. Governance must keep pace with changes in third-party risk management (TPRM), DevSecOps, cloud infrastructure, artificial intelligence, and evolving customer expectations. Strategic, technological, and cultural transformation in digital enterprises also requires strong change leadership. CWLs must become champions of digital enterprise change by aligning governance models with innovation, supporting secure experimentation, and embedding cyber resilience into transformation roadmaps, because CWLs play a critical role in overcoming resistance, cultivating security culture, and ensuring continuous governance maturity.
Table 1: Traditional vs. Digital Enterprises
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
From Shadows to Strategy: Five Core Governance Illusions
1. Chained in Compliance: False Security in Governance
The Shadow: Many organizations equate compliance with security. This illusion becomes a comfortable shadow on the wall: one that leaders are reluctant to turn away from.
Impact: Box-checking behaviors suppress innovation, limit resilience, and blind organizations to emerging threats not covered by existing frameworks like NIST, HITRUST, or ISO.
The CWL Way: A Cybersecurity Warrior Leader cultivates adaptive governance, aligning frameworks with real-time threat intelligence, and transforming compliance into cyber resilience.
2. Fear-Based Leadership and Information Hoarding
The Shadow: Authoritarian leadership or turf protection suppresses collaboration and transparency. This mirrors the prisoners’ reluctance to share knowledge about the real world outside the cave.
Impact: Information silos and fear-based reporting distort risk awareness, delay breach response, and degrade cross-functional alignment between security, legal, IT, and business units.
The CWL Way: CWLs act as trusted guides and boundary spanners, building horizontal bridges and coaching leaders to engage through psychological safety, visibility, and shared accountability.
3. Change Aversion and Legacy Thinking
The Shadow: Legacy systems and sunk-cost biases lock organizations into outdated security models comforting yet dangerously obsolete shadows.
Impact: Organizations fail to evolve controls and capabilities for AI, zero trust, cloud-native, and IoT environments. Cybersecurity governance stagnates.
The CWL Way: Warrior leaders develop e-organizational change muscles: they champion digital transformation roadmaps, train change agents, and shift governance to real-time, data-driven decision-making.
4. The “Shadow Reporting” Problem
The Shadow: Poor KPIs, vanity metrics, or governance theater (e.g., over-reporting green dashboards) obscure reality from senior leadership and the Board.
Impact: Executives are lulled into a false sense of security. Security teams burn out while real threats go unaddressed.
The CWL Way: CWLs surface “hard truths,” promote truth-telling cultures, and use KPIs that reflect risk-adjusted performance: not PR spin.
5. Shadow Puppeteers: Vendors and Framework Fetishism
The Shadow: Overreliance on vendors or blind adherence to frameworks creates external dependency; someone else defines your governance for you.
Impact: Organizations become reactive, not strategic. Governance is shaped by what’s bought, not what’s needed.
The CWL Way: CWLs own the governance story, customizing frameworks to business models, balancing buy/build decisions, and ensuring governance is internalized not outsourced.
Table 2: From Shadows to Strategy
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Conclusion: Emerging from Plato’s Cave
The greatest threat to cybersecurity may not be external attackers, it may be the internal governance shadows organizations refuse to confront. Cybersecurity Warrior Leaders are not merely compliance enforcers, they are change agents, educators, and strategists. Like the freed prisoner in Plato’s Cave, CWLs must risk discomfort to see clearly and help others do the same. By embracing truth, integrity, transparency, and adaptive governance, CWLs lead organizations out of the cave and into the light of adaptive, resilient, integrated, ethical, and intelligence driven cybersecurity programs that ensure the confidentiality, integrity, and availability of data and protect people, culture, processes, and technology.
References
- Glover, J., Rainwater, K., Jones, G., & Friedman, H. (2002). The dynamics of adaptive leadership: A theoretical framework and training model for transforming organizations. Center for Creative Leadership.
- HITRUST. (2023). HITRUST CSF v11.0 Requirements and Implementation Guide.
- Kane, G. C., Palmer, D., Phillips, A. N., Kiron, D., & Buckley, N. (2015). Strategy, not technology, drives digital transformation. MIT Sloan Management Review and Deloitte University Press.
- Kotter, J. P. (1996). Leading Change. Harvard Business School Press.
- NIST. (2024). Cybersecurity Framework 2.0. National Institute of Standards and Technology.
- Plato. (1991). The Republic (A. Bloom, Trans.). Basic Books. (Original work published c. 380 B.C.)
- Schein, E. H. (2010). Organizational Culture and Leadership (4th ed.). Jossey-Bass.
- Weill, P., & Woerner, S. L. (2015). Thriving in an increasingly digital ecosystem. MIT Sloan Management Review, 56(4), 27–34.
- Westerman, G., Bonnet, D., & McAfee, A. (2014). Leading Digital: Turning Technology into Business Transformation. Harvard Business Review Press.
- Bevett, D. L. (2025). Cybersecurity Warrior Leadership and the American Warrior Tradition [Unpublished work].
The content provided herein is for general informational purposes only and should not be construed as legal, regulatory, compliance, or cybersecurity advice. Organizations should consult their own legal, compliance, or cybersecurity professionals regarding specific obligations and risk management strategies. While LevelBlue’s Managed Threat Detection and Response solutions are designed to support threat detection and response at the endpoint level, they are not a substitute for comprehensive network monitoring, vulnerability management, or a full cybersecurity program.

