When corporate data is exposed on a dedicated leak site, the consequences linger long after the attack fades from the news cycle
12 Feb 2026
•
,
6 min. read

In the realm of cybercrime, change is arguably the only constant. While cyber-extortion as a broader category of crime has proved its staying power, ransomware – its arguably most damaging ‘flavor’ – doesn’t live or die on encryption alone. The playbook of ‘yore’ largely involved locking files or systems and demanding payment for a decryption key, but in recent years campaigns switched to combining encryption with data exfiltration and threats to publish the stolen information.
This is where dedicated leak sites, or data leak sites (DLSs), come in. First appearing in late 2019, DLSs have since become the backbone of the double extortion strategy. Threat actors steal corporate data (before encrypting it) and then weaponize the loot publicly, effectively turning a security incident into a full-blown public crisis.
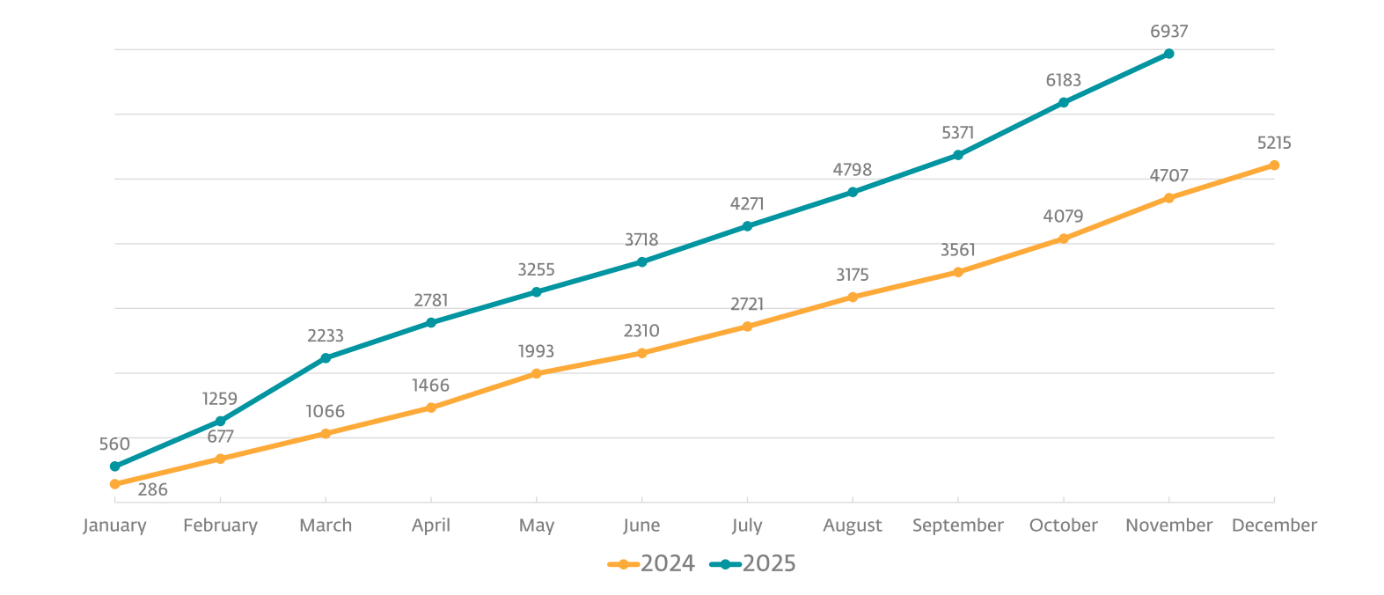
Security experts and law enforcement have, of course, been tracking this shift for years. The FBI and CISA now routinely describe ransomware as a “data theft and extortion” problem. Public tracking projects such as Ransomware.live point in the same direction, even if precise victim counts should be treated with caution. The leak sites reflect only what criminals choose to ‘advertise’, not the full universe of incidents.
Let’s examine the role of DLSs in the ransomware ecosystem and the implications for victim organizations.
How do ransomware groups use data leak sites?
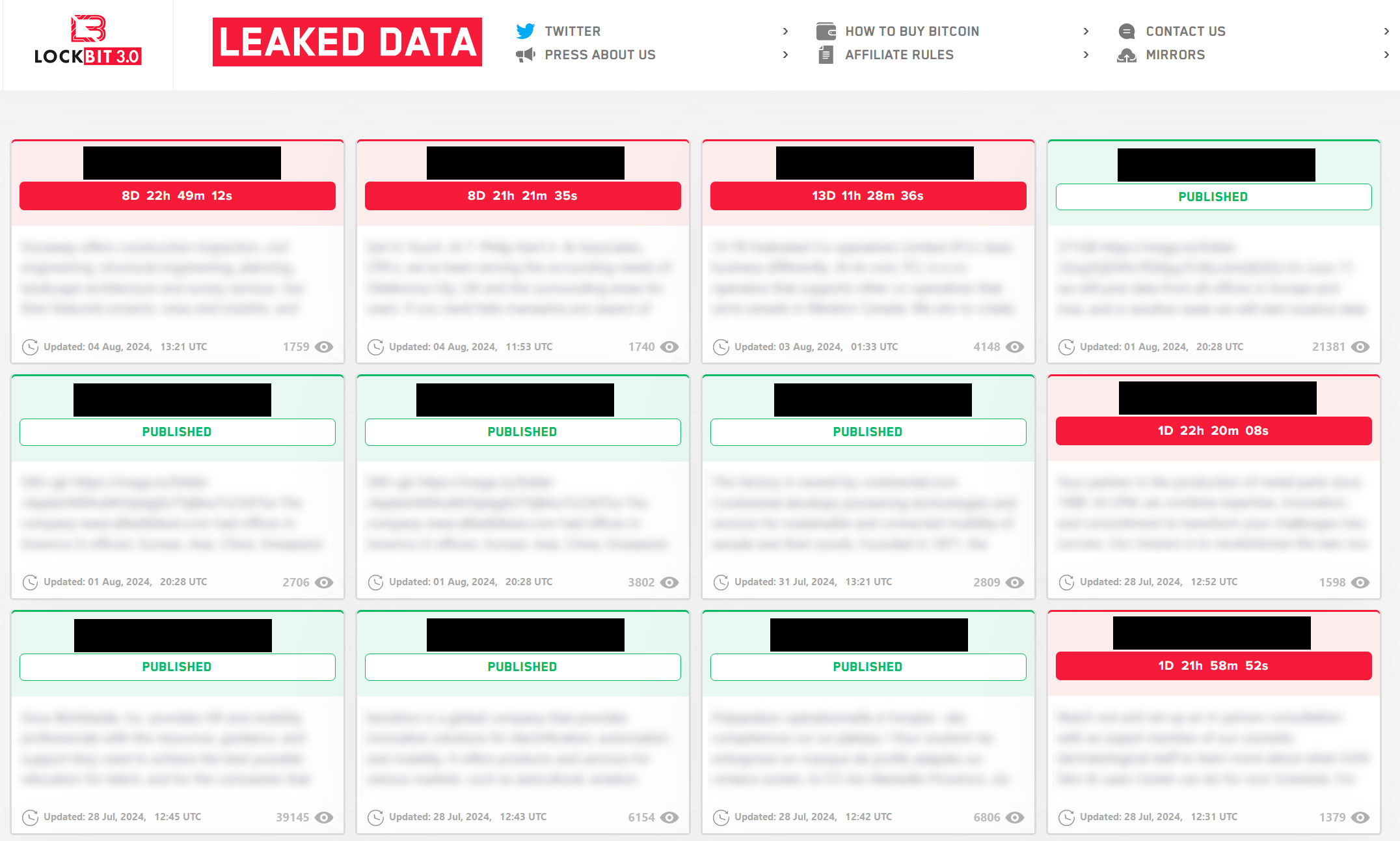
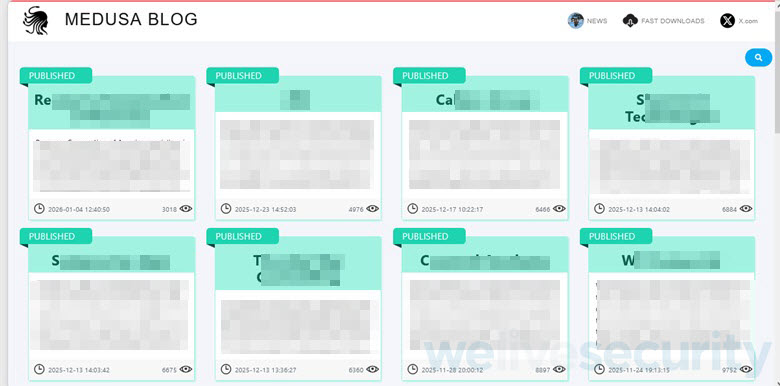
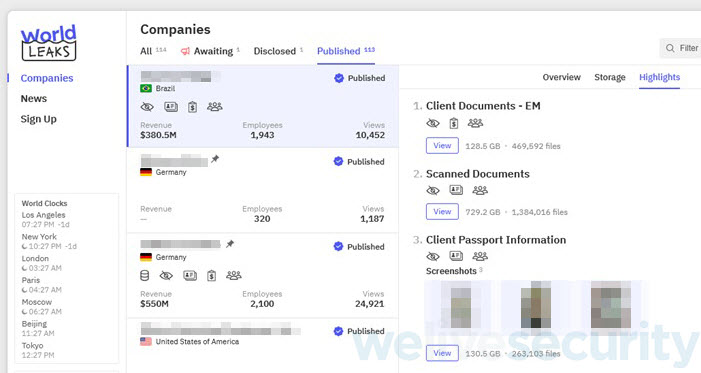
Hosted on the dark web and accessible through the Tor network, the sites often publish a sample of stolen data and threaten victims with full public disclosure unless payment is made. Sometimes the material is published after the victim refused to cave in, thus further turning the screw on them. Information about the victims, the extent of stolen material and even deadlines that are meant to feel inexorable are all part of the strategy.
What makes the strategy devastating is speed and amplification. Once the incident is in the open, multiple risks are collapsed into a single, highly visible moment and the victim organization operates under a cloud of suspicion and uncertainty – often even before its IT and security staff have a full picture of what was stolen or how far the intrusion spread. And that is, of course, the point – data leak sites are a coercion tool.
This is also why they’re carefully curated. Attackers often publish just enough material to show that they are not bluffing: a handful of contracts or a tranche of emails. More is coming unless the victim caves in.
Indeed, the damage rarely stops with the initial victim. The data, once dumped or resold, becomes fuel for follow-on crime, and security teams see it reappear in phishing kits, business email compromise (BEC) campaigns, and identity fraud schemes. In supply-chain incidents, one breach can ripple outward, exposing the victim’s customers and partners. This cascading effect is partly why authorities treat ransomware as a systemic risk, rather than a series of isolated mishaps.
Pressure by design
Every element of a leak site is designed to maximize psychological pressure.
- Proof of unauthorized access. The gangs post sample documents, such as contracts and internal emails, to demonstrate that the intrusion was real and the threat is credible.
- Urgency: Timers and countdowns instill the feeling that time is running out as decisions made under time pressure are more likely to favor the party that controls the clock.
- Public exposure: Even if the stolen data is never released publicly, the mere association with a breach triggers reputational harm that can take years to repair.
- Regulatory risk: Under frameworks like GDPR, HIPAA, and an expanding patchwork of state-level privacy laws in the US, a confirmed breach involving personal data can trigger mandatory disclosures, investigations, and fines..
Beyond extortion
Some ransomware-as-a-service (RaaS) operators have expanded what leak sites do. LockBit, before its infrastructure was seized by law enforcement in early 2024, ran a bug bounty program on its leak site, offering payments to anyone who found vulnerabilities in their code.
Others post ‘gigs’ for corporate insiders, offering payment to employees willing to provide login credentials or weaken security controls. Still other sites double as onboarding platforms for the next wave of attackers as attackers advertise ‘affiliate programs’, explaining the revenue split and how to apply.
Zooming out
Data leak sites work because they hit companies’ weak spots that go beyond technology. A potential data leak triggers multiple risks at once: reputational damage, lost trust among customers and partners, financial hits, regulatory sanctions, and litigation.
As ransomware gangs also sell the stolen information, they feed markets for stolen data and enable follow-on attacks. Some groups have even been spotted skipping encryption entirely and instead ‘only’ grab data and threaten to publish it.
The victims, meanwhile, have to make decisions without enough time to think about the consequences. The people whose personal information is caught up in the incident face a long tail of cleanup, possible account takeovers and identity fraud.
Against that backdrop, paying up might look like the (relatively) easy way out or the least bad option. It is neither. Payment doesn’t guarantee file or system recovery, nor does it guarantee that the data stays private. Many organizations that paid up were hit again within months. And every payment helps fund the next attack.
For organizations, the ransomware threat demands comprehensive defensive measures, which include:
- Deploying advanced security solutions with EDR/XDR/MDR capabilities. Among other things, they monitor anomalous behavior, such as unauthorized process execution and suspicious lateral movement, to stop the threat in its tracks. Indeed, the products are a thorn in criminals‘ sides, who increasingly deploy EDR killers in an attempt to terminate or crash security products, typically by abusing vulnerable drivers.
- Restricting lateral movement through well-defined, stringent access controls. Zero-Trust principles enhance a company’s security posture by eliminating default trust assumptions for any entity. Threat actors often exploit compromised login credentials and remote desktop protocol access to manually navigate networks.
- Keep all your software up-to-date. Known vulnerabilities are one of the primary entry vectors for ransomware actors.
- Maintaining backups stored in isolated, air-gapped environments that ransomware cannot access or modify. Ransomware’s primary objective is to locate and encrypt sensitive data. Worse, even when victims pay ransoms, flawed decryption processes can result in permanent data loss, not to mention other possible ramifications of paying the ransom. Resilient backups and ransomware remediation capabilities go a long way towards mitigating damage from the threat.
- Human vigilance, further refined by well-designed security awareness training, also represents a highly effective defensive barrier. An employee who can spot a malicious email early on removes one of ransomware actors’ favorite entry points, and that alone can markedly cut the risk of an attack victimizing your entire organization.
The ransomware evolution continues unabated as the ransomware-as-a-service (RaaS) model continues to attract a wide criminal user base and grants numerous threats longevity and adaptability. As long as criminals can reliably turn stolen data into a public spectacle, they will keep doing it and ransomware will remain a money machine.


