Long known to be a sweet spot for cybercriminals, small businesses are more likely to be victimized by ransomware than large enterprises
18 Sep 2025
•
,
5 min. read

Think your business is too small to be singled out for digital extortion? Think again. Indeed, if you’re an SMB owner, you’d better assume you’re a potential target. Verizon data reveals that, while ransomware comprises 39% of data breaches at large organizations, the figure rises to 88% for SMBs. Large enterprises may be more prepared to pay multimillion-dollar ransoms, but they’re often also more likely to have the tools and policies in place to prevent, detect and contain breach risk.
Meanwhile, SMB are, much like large corporations, entirely dependent on their data and IT infrastructure to operate. The threat of permanent data loss and a total business shutdown has often been a powerful motivator for paying the ransom fee, even without any guarantee that the business will actually get its data back.
Making matters worse, attackers always look for more levers to force payment, for example via double-extortion attacks where they both steal sensitive data and encrypt and threaten to publish it. Aside from stealing and threatening to leak or wipe sensitive internal data, they might threaten DDoS attacks, regulatory complaints and, oddly enough, even physical violence in some cases. In fact, attackers even happily adjust their ransom demands to increase the odds of a payment, as found by Verizon.
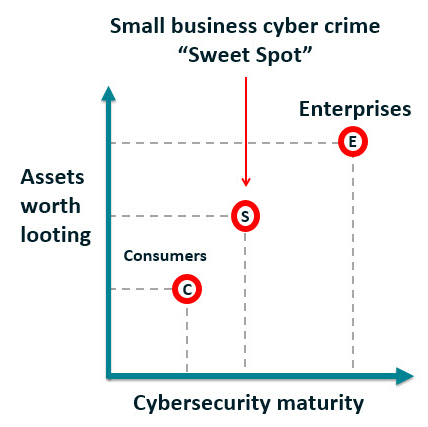
To put it bluntly, less-well defended SMBs are a juicy target for attackers. Indeed, by having more digital assets and money than consumers and fewer cybersecurity protections than enterprises, these businesses have for long been in a “cybercrime sweet spot”. If you’re keen to keep your company’s data safe and systems secure, the good news is that it’s achievable without breaking the bank.
How ransomware groups are evolving
To tackle the threat, you also need to understand who or what’s driving it, and how it’s changing. For one thing, the ransomware-as-a-service (RaaS) industrialization of cybercrime has lowered the barriers to entry and facilitated the proliferation of ransomware. Meanwhile, the turnover of ransomware brands also continues apace, caused in part by intensifying law enforcement efforts. As soon as a group is taken down, a new one often emerges with similar or other tactics and tools in a bid to escape scrutiny. Additionally, fast-evolving TTPs make it harder to mitigate risk.
On the other hand, ransomware rebrands may also be a reflection of the difficulties many groups are having in turning a profit. An analysis of cryptocurrency ransom payments reveals a 35% decrease between 2023 and 2024. Yet faced with potentially fewer victims willing to pay, ransomware groups appear to be doubling down on those who do, as shown by a study claiming that 55% of organizations that paid a ransom last year did so multiple times; with 29% paying three or more times.
How AI is transforming ransomware
As technology advances, ransomware groups are also changing tack to increase their chances of success. The usual ways to achieve initial access into victim networks remain vulnerability exploitation, phishing and remote access compromise; such as via credentials obtained by infostealer malware. Yet AI tools could supercharge all of these efforts.
The UK’s National Cyber Security Centre (NCSC) warned recently that over the next two years AI use will lead to “an increase in frequency and intensity of cyber threats.” Scanning for vulnerable victims (reconnaissance), vulnerability exploitation, and social engineering in particular will become more democratized on the cybercrime underground.
Meanwhile, ESET recently discovered what’s believed to be the world’s first AI-powered ransomware, “PromptLock.” It uses a legitimate model from OpenAI to generate malicious scripts. “The prospect of AI-powered malware that can, among other things, adapt to the environment and change its tactics on the fly may generally represent a new frontier in cyberattacks,” ESET warns.
A separate ESET report highlights other new developments including the appearance of “EDR killers” – designed to terminate, blind, or crash endpoint detection and response (EDR) tooling installed on victim systems. Groups have also been observed using “ClickFix” social engineering tactics to trick users into installing malware on their machines.
How to protect your business
A handful of SMBs know to their cost what can happen following a ransomware breach. Although already under financial pressure before a 2023 attack, British logistics firm KNP subsequently fell into administration with the loss of 700 jobs.
To prevent your business going the same way, adopt a prevention-first mindset by:
- Deploying robust patch management to ensure vulnerabilities deemed the highest risk are patched, to further limit the opportunity for initial access and lateral movement.
- Updating identity and access management policies and tooling in line with a Zero Trust approach. This means assuming breach, continuous verification of users, least privilege policies, and multi-factor authentication.
- Ensuring security software from a trusted vendor is placed on all devices, from endpoints, servers to remote worker laptops.
- Backing up sensitive files according to industry best practices, so that even if files are encrypted they can be restored, reducing your adversary’s leverage.
- Devising an incident response plan in collaboration with key stakeholders from across the business. It should also be tested periodically to ensure it’s fit for purpose in helping to accelerate containment following an intrusion.
- Continuously monitoring your networks, endpoints and other parts of the IT environment for signs of suspicious behavior. These early warning signs should help to minimize attacker dwell time.
- Updating training and awareness courses to include simulation exercises featuring the latest phishing tactics, including voice-based phishing (vishing). Your employees are both your best asset and your weakest link.
Importantly, make sure to properly evaluate your assets, resources and risks, including those emanating from supply chains. Keep an inventory of all open-source and proprietary off-the-shelf tools used by your organization. More broadly, asset visibility is the foundation of any risk management program. In other words, attackers are known to count on blind spots. If you don’t know a system exists or what data it holds, you can’t protect it.
As the ESET SMB Digital Security Sentiment 2022 has shown, many SMBs are increasingly aware of ransomware and other risks facing their business, but they don’t have the confidence in their in-house cybersecurity expertise. It makes sense then that many of them, especially those with fewer resources, are increasingly turning to managed detection and response (MDR) services to and hand off the monitoring to an expert partner who then performs 24/7/365 threat hunting, detection and response, reducing the operational burden on your in-house team while ensuring any ransomware activity is rapidly identified, contained and eliminated. Ransomware actors need to be sent packing before they have a chance to cause any damage.


