
A recently discovered ransomware strain called HybridPetya can bypass the UEFI Secure Boot feature to install a malicious application on the EFI System Partition.
HybridPetya appears inspired by the destructive Petya/NotPetya malware that encrypted computers and prevented Windows from booting in attacks in 2016 and 2017 but did not provide a recovery option.
Researchers at cybersecurity company ESET found a sample of HybridPetya on VirusTotal. They note that this may be a research project, a proof-of-concept, or an early version of a cybercrime tool still under limited testing.
Still, ESET says that its presence is yet another example (along with BlackLotus, BootKitty, and Hyper-V Backdoor) that UEFI bootkits with Secure Bypass functionality are a real threat.
HybridPetya incorporates characteristics from both Petya and NotPetya, including the visual style and attack chain of these older malware strains.
However, the developer added new things like installation into the EFI System Partition and the ability to bypass Secure Boot by exploiting the CVE-2024-7344 vulnerability.
ESET discovered the flaw in January this year, The issue consists in Microsoft-signed applications that could be exploited to deploy bootkits even with Secure Boot protection active on the target.
Source: ESET
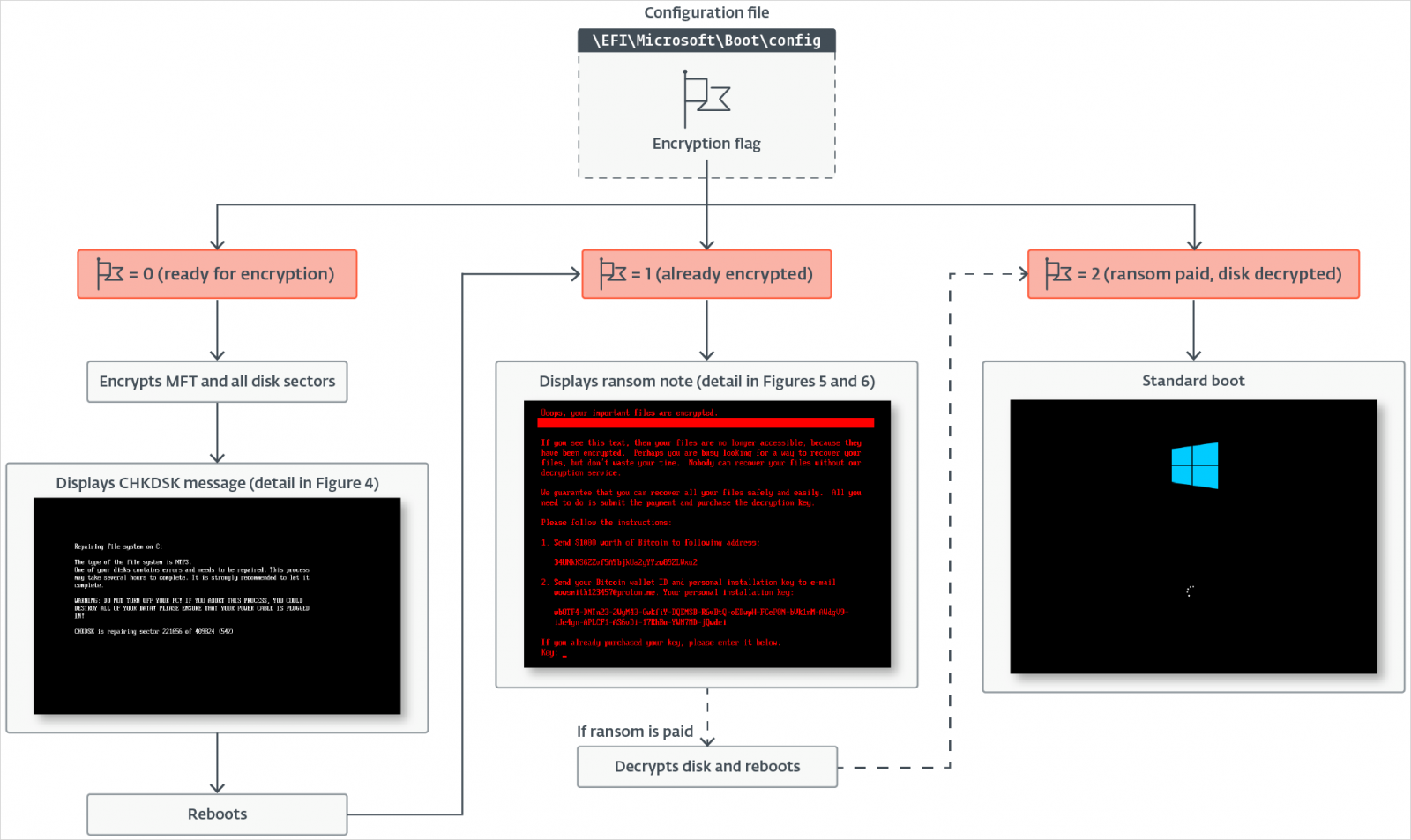
Upon launch, HybridPetya determines if the host uses UEFI with GPT partitioning and drops a malicious bootkit into the EFI System partition consisting of several files.
These include configuration and validation files, a modified bootloader, a fallback UEFI bootloader, an exploit payload container, and a status file that tracks the encryption progress.
ESET lists the following files used across analyzed variants of HybridPetya:
- \EFI\Microsoft\Boot\config (encryption flag + key + nonce + victim ID)
- \EFI\Microsoft\Boot\verify (used to validate correct decryption key)
- \EFI\Microsoft\Boot\counter (progress tracker for encrypted clusters)
- \EFI\Microsoft\Boot\bootmgfw.efi.old (backup of original bootloader)
- \EFI\Microsoft\Boot\cloak.dat (contains XORed bootkit in Secure Boot bypass variant)
Also, the malware replaces \EFI\Microsoft\Boot\bootmgfw.efi with the vulnerable ‘reloader.efi,’ and removes \EFI\Boot\bootx64.efi.
The original Windows bootloader is also saved to be activated in the case of successful restoration, meaning that the victim paid the ransom.
Once deployed, HybridPetya triggers a BSOD displaying a bogus error, as Petya did, and forces a system reboot, allowing the malicious bootkit to execute upon system boot.
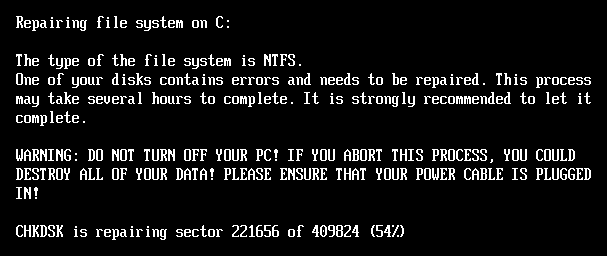
At this step, the ransomware encrypts all MFT clusters using a Salsa20 key and nonce extracted from the config file while displaying a fake CHKDSK message, like NotPetya.
Source: ESET
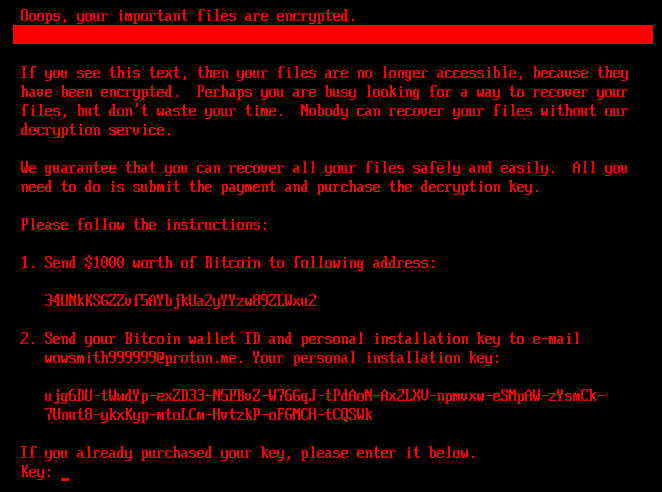
Once the encryption completes, another reboot is triggered and the victim is served a ransom note during system boot, demanding a Bitcoin payment of $1,000.
Source: ESET
In exchange, the victim is provided a 32-character key they can enter on the ransom note screen, which restores the original bootloader, decrypts the clusters, and prompts the user to reboot.
Though HybridPetya has not been observed in any real attacks in the wild, similar projects may choose to weaponize the PoC and use it in broad campaigns targeting unpatched Windows systems at any time.
Indicators of compromise to help defend against this threat have been made available on this GitHub repository.
Microsoft fixed CVE-2024-7344 with the January 2025 Patch Tuesday, so Windows systems that have applied this or later security updates are protected from HybridPetya.
Another solid practice against ransomware is to keep offline backups of your most important data, allowing free and easy system restoration.


