Microsoft on Tuesday announced 63 patches affecting 13 product families. Four of the addressed issues are considered by Microsoft to be of Critical severity, and nine have a CVSS base score of 8.0 or higher. One is known to be under active exploit in the wild, though neither it nor any other issue addressed this month has been publicly disclosed.
At patch time, five CVEs are judged more likely to be exploited in the next 30 days by the company’s estimation, in addition to the one already detected to be so. Various of this month’s issues are amenable to direct detection by Sophos protections, and we include information on those in a table below.
The slippery CVE count this month could reflect overflow from last month’s record-setting release. Two Important-severity Windows CVEs, CVE-2025-62208 and CVE-2025-62209, actually shipped in October, but were not mentioned in the information released by Microsoft at that time. For those who have already applied October’s patches, these two CVEs are already on your system, leaving just 61 patches for November. For the purposes of this post, however, we are including both of those CVEs in our November counts simply to make sure they get counted at all.
In a similar vein, five Chrome-issued patches relevant to Edge were patched earlier in the month. We have included information on those patches, along with 10 Adobe fixes related to ColdFusion and the usual Servicing Stack, in Appendix D.
We are as always including at the end of this post appendices listing all Microsoft’s patches sorted by severity (Appendix A), by predicted exploitability timeline and CVSS Base score (Appendix B), and by product family (Appendix C). Appendix E provides a breakout of the patches affecting the various Windows Server platforms.
By the numbers
- Total CVEs: 63
- Publicly disclosed: 0
- Exploit detected: 1
- Severity
- Critical: 4
- Important: 59
- Impact
- Denial of Service: 3
- Elevation of Privilege: 29
- Information Disclosure: 11
- Remote Code Execution: 16
- Security Feature Bypass: 2
- Spoofing: 2
- CVSS Base score 9.0 or greater: 1
- CVSS Base score 8.0 or greater: 9
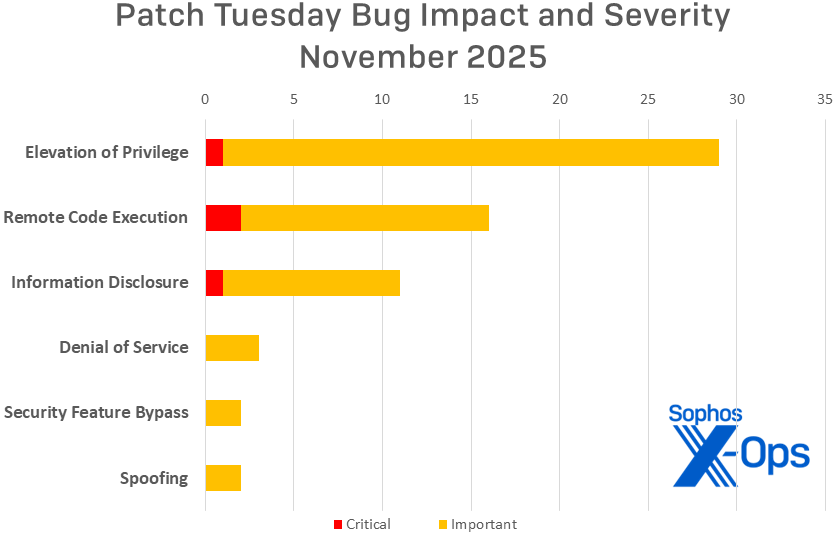
Figure 1: Elevation of Privilege issues continue to dominate the Patch Tuesday numbers
Products
- Windows: 38
- Office: 12
- 365: 11
- Excel: 7
- Visual Studio: 4
- Dynamics 365: 3
- Azure: 1
- Configuration Manager: 1
- Nuance PowerScribe 360: 1
- OneDrive for Android: 1
- SharePoint: 1
- SQL: 1
- Windows Subsystem for Linux: 1
As is our custom for this list, CVEs that apply to more than one product family are counted once for each family they affect. We note, by the way, that CVE names don’t always reflect affected product families closely. In particular, some CVEs names in the Office family may mention products that don’t appear in the list of products affected by the CVE, and vice versa.

Figure 2: Just 13 product families are touched by November’s patches, and some of the omissions are striking – for instance, note that though there are four Visual Studio fixes, none of those apply to .NET. Meanwhile, 34 of this month’s 38 Windows patches apply to Windows 10, for which Microsoft “ended support” with great fanfare in October
Notable November updates
In addition to the issues discussed above, a variety of specific items merit attention.
CVE-2025-62199 — Microsoft Office Remote Code Execution Vulnerability
CVE-2025-62214 — Visual Studio Remote Code Execution Vulnerability
All four Critical-severity issues in this month’s release are judged by Microsoft to be less likely to come under active exploitation within the next 30 days. Two of them are nonetheless of interest due to their ease of exploitation – or lack thereof. The Office vulnerability, a use-after-free issue that would allow a successful attacker to run code locally, is the only one among all this month’s Office issues to have Preview Pane as an attack vector. Meanwhile, the Visual Studio issue is unusually hard to exploit; notes Microsoft, “exploitation is not trivial for this vulnerability as it requires multiple steps — prompt injection, Copilot Agent interaction, and triggering a build.” Whew.
CVE-2025-60724 — GDI+ Remote Code Execution Vulnerability
The only CVE this month to merit a CVSS Base score above 9.0, this heap-based buffer overflow issue affects both Office and Windows. Microsoft assigns this issue only an Important-level severity and deems it less likely to see active exploit within the next 30 days. Why the discrepancy? Microsoft explains that the difference lies within the multiple vectors by which this issue could be exploited: “An attacker could trigger this vulnerability by convincing a victim to download and open a document that contains a specially crafted metafile. In the worst-case scenario, an attacker could trigger this vulnerability on web services by uploading documents containing a specially crafted metafile without user interaction. When multiple attack vectors can be used, we assign a score based on the scenario with the higher risk.”
CVE-2025-30398 — Nuance PowerScribe 360 Information Disclosure Vulnerability
CVE-2025-60722 — Microsoft OneDrive for Android Elevation of Privilege Vulnerability
Two wildly dissimilar patches – one addressing a Critical-severity bug in extremely specialized medical software, one an Important-severity issue in a package with over five billion downloads so far – but they share an unusual path to resolution, as affected users have to get these updates outside the usual Microsoft patching mechanisms. Nuance users are asked to reach out to their Customer Success Manager (CSM) or Technical Support – yes, get in touch with actual humans – to obtain their updates. The other five billion of us, meanwhile, will be heading for the Google App Store to pick up our patch, though hopefully not all at the same time.

Figure 3: With one month to go in 2025, Elevation of Privilege CVEs continue to dominate the patch counts
Sophos protections
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2025-59512 | Exp/2559512-A | Exp/2559512-A |
| CVE-2025-60705 | Exp/2560705-A | Exp/2560705-A |
| CVE-2025-60719 | Exp/2560719-A | Exp/2560719-A |
| CVE-2025-62213 | Exp/2562213-A | Exp/2562213-A |
| CVE-2025-62215 | Exp/2562215-A | Exp/2562215-A |
As you can every month, if you don’t want to wait for your system to pull down Microsoft’s updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows you’re running, then download the Cumulative Update package for your specific system’s architecture and build number.
Appendix A: Vulnerability Impact and Severity
This is a list of November patches sorted by impact, then sub-sorted by severity. Each list is further arranged by CVE.
Elevation of Privilege (29 CVEs)
| Critical severity | |
| CVE-2025-60716 | DirectX Graphics Kernel Elevation of Privilege Vulnerability |
| Important severity | |
| CVE-2025-47179 | Configuration Manager Elevation of Privilege Vulnerability |
| CVE-2025-59499 | Microsoft SQL Server Elevation of Privilege Vulnerability |
| CVE-2025-59505 | Windows Smart Card Reader Elevation of Privilege Vulnerability |
| CVE-2025-59506 | DirectX Graphics Kernel Elevation of Privilege Vulnerability |
| CVE-2025-59507 | Windows Speech Runtime Elevation of Privilege Vulnerability |
| CVE-2025-59508 | Windows Speech Recognition Elevation of Privilege Vulnerability |
| CVE-2025-59511 | Windows WLAN Service Elevation of Privilege Vulnerability |
| CVE-2025-59512 | Customer Experience Improvement Program (CEIP) Elevation of Privilege Vulnerability |
| CVE-2025-59514 | Microsoft Streaming Service Proxy Elevation of Privilege Vulnerability |
| CVE-2025-59515 | Windows Broadcast DVR User Service Elevation of Privilege Vulnerability |
| CVE-2025-60703 | Windows Remote Desktop Services Elevation of Privilege Vulnerability |
| CVE-2025-60704 | Windows Kerberos Elevation of Privilege Vulnerability |
| CVE-2025-60705 | Windows Client-Side Caching Elevation of Privilege Vulnerability |
| CVE-2025-60707 | Multimedia Class Scheduler Service (MMCSS) Driver Elevation of Privilege Vulnerability |
| CVE-2025-60709 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2025-60710 | Host Process for Windows Tasks Elevation of Privilege Vulnerability |
| CVE-2025-60713 | Windows Routing and Remote Access Service (RRAS) Elevation of Privilege Vulnerability |
| CVE-2025-60717 | Windows Broadcast DVR User Service Elevation of Privilege Vulnerability |
| CVE-2025-60718 | Windows Administrator Protection Elevation of Privilege Vulnerability |
| CVE-2025-60719 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2025-60720 | Windows Transport Driver Interface (TDI) Translation Driver Elevation of Privilege Vulnerability |
| CVE-2025-60721 | Windows Administrator Protection Elevation of Privilege Vulnerability |
| CVE-2025-60722 | Microsoft OneDrive for Android Elevation of Privilege Vulnerability |
| CVE-2025-62213 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2025-62215 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2025-62217 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2025-62218 | Microsoft Wireless Provisioning System Elevation of Privilege Vulnerability |
| CVE-2025-62219 | Microsoft Wireless Provisioning System Elevation of Privilege Vulnerability |
Remote Code Execution (16 CVEs)
| Critical severity | |
| CVE-2025-62199 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-62214 | Visual Studio Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2025-59504 | Azure Monitor Agent Remote Code Execution Vulnerability |
| CVE-2025-60714 | Windows OLE Remote Code Execution Vulnerability |
| CVE-2025-60715 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2025-60724 | GDI+ Remote Code Execution Vulnerability |
| CVE-2025-60727 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62200 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62201 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62203 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62204 | Microsoft SharePoint Remote Code Execution Vulnerability |
| CVE-2025-62205 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-62216 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-62220 | Windows Subsystem for Linux GUI Remote Code Execution Vulnerability |
| CVE-2025-62222 | Agentic AI and Visual Studio Code Remote Code Execution Vulnerability |
| CVE-2025-62452 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
Information Disclosure (11 CVEs)
| Critical severity | |
| CVE-2025-30398 | Nuance PowerScribe 360 Information Disclosure Vulnerability |
| Important severity | |
| CVE-2025-59240 | Microsoft Excel Information Disclosure Vulnerability |
| CVE-2025-59509 | Windows Speech Recognition Information Disclosure Vulnerability |
| CVE-2025-59513 | Windows Bluetooth RFCOM Protocol Driver Information Disclosure Vulnerability |
| CVE-2025-60706 | Windows Hyper-V Information Disclosure Vulnerability |
| CVE-2025-60726 | Microsoft Excel Information Disclosure Vulnerability |
| CVE-2025-60728 | Microsoft Excel Information Disclosure Vulnerability |
| CVE-2025-62202 | Microsoft Excel Information Disclosure Vulnerability |
| CVE-2025-62206 | Microsoft Dynamics 365 (On-Premises) Information Disclosure Vulnerability |
| CVE-2025-62208 | Windows License Manager Information Disclosure Vulnerability |
| CVE-2025-62209 | Windows License Manager Information Disclosure Vulnerability |
Denial of Service (3 CVEs)
| Important severity | |
| CVE-2025-59510 | Windows Routing and Remote Access Service (RRAS) Denial of Service Vulnerability |
| CVE-2025-60708 | Storvsp.sys Driver Denial of Service Vulnerability |
| CVE-2025-60723 | DirectX Graphics Kernel Denial of Service Vulnerability |
Security Feature Bypass (2 CVEs)
| Important severity | |
| CVE-2025-62449 | Microsoft Visual Studio Code CoPilot Chat Extension Security Feature Bypass Vulnerability |
| CVE-2025-62453 | GitHub Copilot and Visual Studio Code Security Feature Bypass Vulnerability |
Spoofing (2 CVEs)
| Important severity | |
| CVE-2025-62210 | Dynamics 365 Field Service (online) Spoofing Vulnerability |
| CVE-2025-62211 | Dynamics 365 Field Service (online) Spoofing Vulnerability |
Appendix B: Exploitability and CVSS
This is a list of the November CVEs judged by Microsoft to be more likely to be exploited in the wild within the first 30 days post-release. The list is arranged by CVE.
| Exploitation more likely within the next 30 days | |
| CVE-2025-59512 | Customer Experience Improvement Program (CEIP) Elevation of Privilege Vulnerability |
| CVE-2025-60705 | Windows Client-Side Caching Elevation of Privilege Vulnerability |
| CVE-2025-60719 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2025-62213 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2025-62217 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
The CVE listed below was known to be under active exploit prior to the release of this month’s patches.
| CVE-2025-62215 | Windows Kernel Elevation of Privilege Vulnerability |
These are the November CVEs with a Microsoft-assessed CVSS Base score of 8.0 or higher. They are arranged by score and further sorted by CVE. For more information on how CVSS works, please see our series on patch prioritization schema.
| CVSS Base | CVSS Temporal | CVE | Title |
| 9.8 | 8.5 | CVE-2025-60724 | GDI+ Remote Code Execution Vulnerability |
| 8.8 | 7.7 | CVE-2025-59499 | Microsoft SQL Server Elevation of Privilege Vulnerability |
| 8.8 | 7.7 | CVE-2025-62220 | Windows Subsystem for Linux GUI Remote Code Execution Vulnerability |
| 8.8 | 7.7 | CVE-2025-62222 | Agentic AI and Visual Studio Code Remote Code Execution Vulnerability |
| 8.7 | 7.6 | CVE-2025-62211 | Dynamics 365 Field Service (online) Spoofing Vulnerability |
| 8.1 | 7.1 | CVE-2025-30398 | Nuance PowerScribe 360 Information Disclosure Vulnerability |
| 8.0 | 7.0 | CVE-2025-60715 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| 8.0 | 7.0 | CVE-2025-62204 | Microsoft SharePoint Remote Code Execution Vulnerability |
| 8.0 | 7.0 | CVE-2025-62452 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
Appendix C: Products Affected
This is a list of November’s patches sorted by product family, then sub-sorted by severity. Each list is further arranged by CVE. Patches that are shared among multiple product families are listed multiple times, once for each product family. Certain issues for which advisories have been issued are covered in Appendix D, and issues affecting Windows Server are further sorted in Appendix E. All CVE titles are accurate as made available by Microsoft; for further information on why certain products may appear in titles and not product families (or vice versa), please consult Microsoft.
Windows (38 CVEs)
| Critical severity | |
| CVE-2025-60716 | DirectX Graphics Kernel Elevation of Privilege Vulnerability |
| Important severity | |
| CVE-2025-59505 | Windows Smart Card Reader Elevation of Privilege Vulnerability |
| CVE-2025-59506 | DirectX Graphics Kernel Elevation of Privilege Vulnerability |
| CVE-2025-59507 | Windows Speech Runtime Elevation of Privilege Vulnerability |
| CVE-2025-59508 | Windows Speech Recognition Elevation of Privilege Vulnerability |
| CVE-2025-59509 | Windows Speech Recognition Information Disclosure Vulnerability |
| CVE-2025-59510 | Windows Routing and Remote Access Service (RRAS) Denial of Service Vulnerability |
| CVE-2025-59511 | Windows WLAN Service Elevation of Privilege Vulnerability |
| CVE-2025-59512 | Customer Experience Improvement Program (CEIP) Elevation of Privilege Vulnerability |
| CVE-2025-59513 | Windows Bluetooth RFCOM Protocol Driver Information Disclosure Vulnerability |
| CVE-2025-59514 | Microsoft Streaming Service Proxy Elevation of Privilege Vulnerability |
| CVE-2025-59515 | Windows Broadcast DVR User Service Elevation of Privilege Vulnerability |
| CVE-2025-60703 | Windows Remote Desktop Services Elevation of Privilege Vulnerability |
| CVE-2025-60704 | Windows Kerberos Elevation of Privilege Vulnerability |
| CVE-2025-60705 | Windows Client-Side Caching Elevation of Privilege Vulnerability |
| CVE-2025-60706 | Windows Hyper-V Information Disclosure Vulnerability |
| CVE-2025-60707 | Multimedia Class Scheduler Service (MMCSS) Driver Elevation of Privilege Vulnerability |
| CVE-2025-60708 | Storvsp.sys Driver Denial of Service Vulnerability |
| CVE-2025-60709 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2025-60710 | Host Process for Windows Tasks Elevation of Privilege Vulnerability |
| CVE-2025-60713 | Windows Routing and Remote Access Service (RRAS) Elevation of Privilege Vulnerability |
| CVE-2025-60714 | Windows OLE Remote Code Execution Vulnerability |
| CVE-2025-60715 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2025-60717 | Windows Broadcast DVR User Service Elevation of Privilege Vulnerability |
| CVE-2025-60718 | Windows Administrator Protection Elevation of Privilege Vulnerability |
| CVE-2025-60719 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2025-60720 | Windows Transport Driver Interface (TDI) Translation Driver Elevation of Privilege Vulnerability |
| CVE-2025-60721 | Windows Administrator Protection Elevation of Privilege Vulnerability |
| CVE-2025-60723 | DirectX Graphics Kernel Denial of Service Vulnerability |
| CVE-2025-60724 | GDI+ Remote Code Execution Vulnerability |
| CVE-2025-62208 | Windows License Manager Information Disclosure Vulnerability |
| CVE-2025-62209 | Windows License Manager Information Disclosure Vulnerability |
| CVE-2025-62213 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2025-62215 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2025-62217 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2025-62218 | Microsoft Wireless Provisioning System Elevation of Privilege Vulnerability |
| CVE-2025-62219 | Microsoft Wireless Provisioning System Elevation of Privilege Vulnerability |
| CVE-2025-62452 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
Office (12 CVEs)
| Critical severity | |
| CVE-2025-62199 | Microsoft Office Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2025-59240 | Microsoft Excel Information Disclosure Vulnerability |
| CVE-2025-60724 | GDI+ Remote Code Execution Vulnerability |
| CVE-2025-60726 | Microsoft Excel Information Disclosure Vulnerability |
| CVE-2025-60727 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-60728 | Microsoft Excel Information Disclosure Vulnerability |
| CVE-2025-62200 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62201 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62202 | Microsoft Excel Information Disclosure Vulnerability |
| CVE-2025-62203 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62205 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-62216 | Microsoft Office Remote Code Execution Vulnerability |
365 (11 CVEs)
| Critical severity | |
| CVE-2025-62199 | Microsoft Office Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2025-59240 | Microsoft Excel Information Disclosure Vulnerability |
| CVE-2025-60726 | Microsoft Excel Information Disclosure Vulnerability |
| CVE-2025-60727 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-60728 | Microsoft Excel Information Disclosure Vulnerability |
| CVE-2025-62200 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62201 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62202 | Microsoft Excel Information Disclosure Vulnerability |
| CVE-2025-62203 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62205 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2025-62216 | Microsoft Office Remote Code Execution Vulnerability |
Excel (7 CVEs)
| Important severity | |
| CVE-2025-59240 | Microsoft Excel Information Disclosure Vulnerability |
| CVE-2025-60726 | Microsoft Excel Information Disclosure Vulnerability |
| CVE-2025-60727 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62200 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62201 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2025-62202 | Microsoft Excel Information Disclosure Vulnerability |
| CVE-2025-62203 | Microsoft Excel Remote Code Execution Vulnerability |
Visual Studio (4 CVEs)
| Critical severity | |
| CVE-2025-62214 | Visual Studio Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2025-62222 | Agentic AI and Visual Studio Code Remote Code Execution Vulnerability |
| CVE-2025-62449 | Microsoft Visual Studio Code CoPilot Chat Extension Security Feature Bypass Vulnerability |
| CVE-2025-62453 | GitHub Copilot and Visual Studio Code Security Feature Bypass Vulnerability |
Dynamics 365 (3 CVEs)
| Important severity | |
| CVE-2025-62206 | Microsoft Dynamics 365 (On-Premises) Information Disclosure Vulnerability |
| CVE-2025-62210 | Dynamics 365 Field Service (online) Spoofing Vulnerability |
| CVE-2025-62211 | Dynamics 365 Field Service (online) Spoofing Vulnerability |
Azure (1 CVE)
| Important severity | |
| CVE-2025-59504 | Azure Monitor Agent Remote Code Execution Vulnerability |
Configuration Manager (1 CVE)
| Important severity | |
| CVE-2025-47179 | Configuration Manager Elevation of Privilege Vulnerability |
Nuance PowerScribe 360 (1 CVE)
| Critical severity | |
| CVE-2025-30398 | Nuance PowerScribe 360 Information Disclosure Vulnerability |
OneDrive for Android (1 CVE)
| Important severity | |
| CVE-2025-60722 | Microsoft OneDrive for Android Elevation of Privilege Vulnerability |
SharePoint (1 CVE)
| Important severity | |
| CVE-2025-62204 | Microsoft SharePoint Remote Code Execution Vulnerability |
SQL (1 CVE)
| Important severity | |
| CVE-2025-59499 | Microsoft SQL Server Elevation of Privilege Vulnerability |
Windows Subsystem for Linux (1 CVE)
| Important severity | |
| CVE-2025-62220 | Windows Subsystem for Linux GUI Remote Code Execution Vulnerability |
Appendix D: Advisories and Other Products
There are 5 Edge-related advisories in November’s release, all of which originated with Chrome.
| CVE-2025-12725 | Chromium: CVE-2025-12725 Out of bounds write in WebGPU |
| CVE-2025-12726 | Chromium: CVE-2025-12726 Inappropriate implementation in Views. |
| CVE-2025-12727 | Chromium: CVE-2025-12727 Inappropriate implementation in V8 |
| CVE-2025-12728 | Chromium: CVE-2025-12728 Inappropriate implementation in Omnibox |
| CVE-2025-12729 | Chromium: CVE-2025-12729 Inappropriate implementation in Omnibox |
This month also includes the periodic Servicing Stack updates, ADV990001.
Adobe is also releasing patches for ten ColdFusion issues today with Bulletin APSB25-105:
| Critical severity | |
| CVE-2025-61808 | Unrestricted Upload of File with Dangerous Type (CWE-434) |
| CVE-2025-61809 | Improper Input Validation (CWE-20) |
| CVE-2025-61810 | Deserialization of Untrusted Data (CWE-502) |
| CVE-2025-61811 | Improper Access Control (CWE-284) |
| CVE-2025-61812 | Improper Input Validation (CWE-20) |
| CVE-2025-61813 | Improper Restriction of XML External Entity Reference (‘XXE’) (CWE-611) |
| CVE-2025-61830 | Deserialization of Untrusted Data (CWE-502) |
| Important severity | |
| CVE-2025-61821 | Improper Restriction of XML External Entity Reference (‘XXE’) (CWE-611) |
| CVE-2025-61822 | Improper Input Validation (CWE-20) |
| CVE-2025-61823 | Improper Restriction of XML External Entity Reference (‘XXE’) (CWE-611) |
Appendix E: Affected Windows Server versions
This is a table of the 33 CVEs in the November release affecting Windows Server versions 2008 through 2025. The table differentiates among major versions of the platform but doesn’t go into deeper detail (eg., Server Core). Critical-severity issues are marked in red; an “x” indicates that the CVE does not apply to that version. Administrators are encouraged to use this appendix as a starting point to ascertain their specific exposure, as each reader’s situation, especially as it concerns products out of mainstream support, will vary. For specific Knowledge Base numbers, please consult Microsoft.
| CVE | S-08 | S-08r2 | S-12 | 12r2 | S-16 | S-19 | S-22 | 23h2 | S-25 |
| CVE-2025-59505 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-59506 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-59507 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-59508 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-59509 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-59510 | × | × | × | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-59511 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-59512 | × | × | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-59513 | ■ | ■ | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-59514 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-59515 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2025-60703 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-60704 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-60705 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-60706 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-60707 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-60708 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-60709 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-60713 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-60714 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | × |
| CVE-2025-60715 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-60716 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-60717 | × | × | × | × | × | ■ | × | ■ | ■ |
| CVE-2025-60719 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-60720 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-60723 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-60724 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-62208 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-62209 | × | × | × | × | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-62213 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-62215 | × | × | × | × | × | ■ | ■ | ■ | ■ |
| CVE-2025-62217 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |
| CVE-2025-62452 | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ | ■ |

