
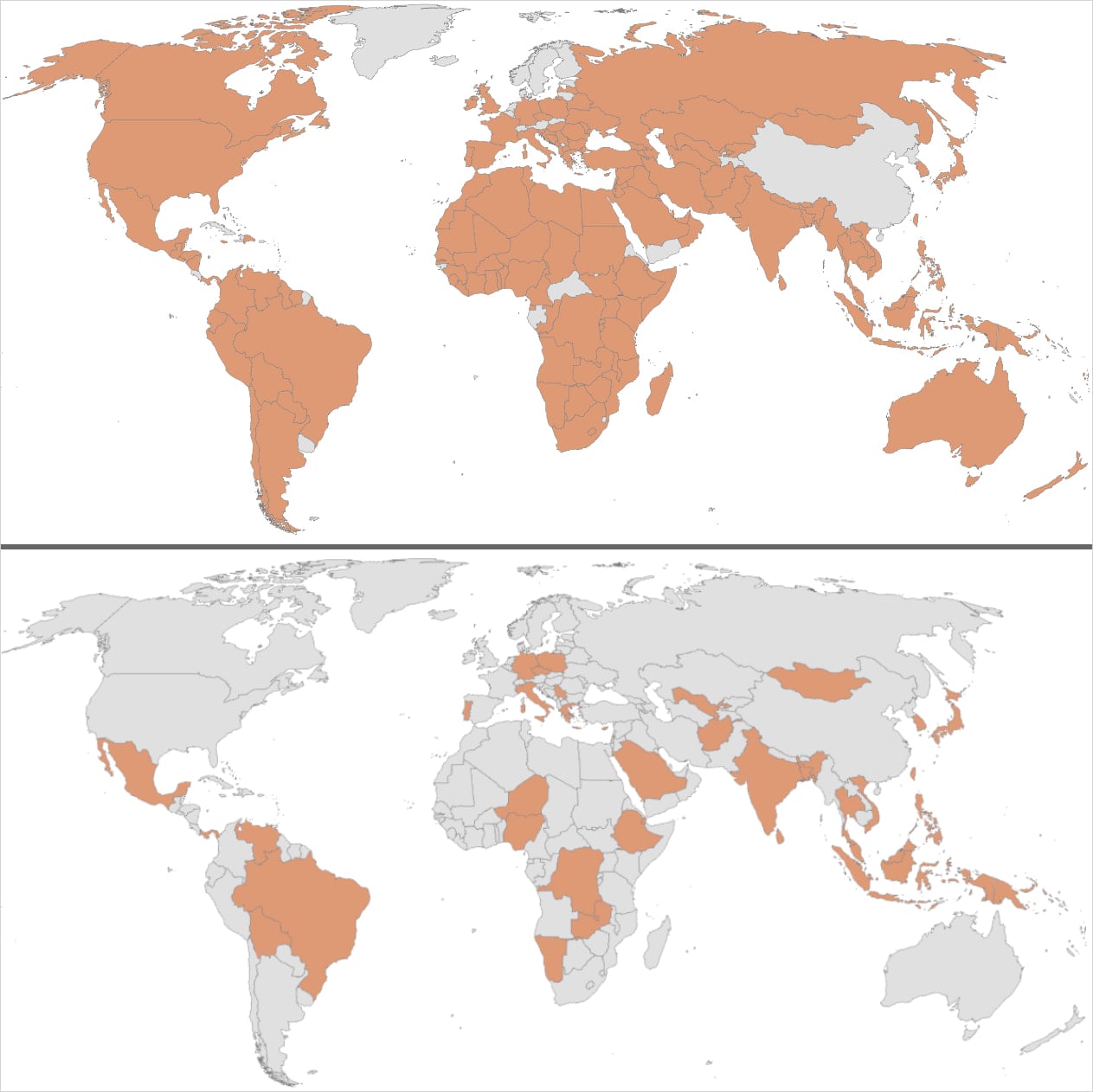
A state-sponsored threat group has compromised dozens of networks of government and critical infrastructure entities in 37 countries in global-scale operations dubbed ‘Shadow Campaigns’.
Between November and December last year, the actor also engaged in reconnaissance activity targeting government entities connected to 155 countries.
According to Palo Alto Networks’ Unit 42 division, the group has been active since at least January 2024, and there is high confidence that it operates from Asia. Until definitive attribution is possible, the researchers track the actor as TGR-STA-1030/UNC6619.
‘Shadow Campaigns’ activity focuses primarily on government ministries, law enforcement, border control, finance, trade, energy, mining, immigration, and diplomatic agencies.
Unit 42 researchers confirmed that the attacks successfully compromised at least 70 government and critical infrastructure organizations across 37 countries.
This includes organizations engaged in trade policy, geopolitical issues, and elections in the Americas; ministries and parliaments across multiple European states; the Treasury Department in Australia; and government and critical infrastructure in Taiwan.
Source: Unit 42
The list of countries with targeted or compromised organizations is extensive and focused on certain regions with particular timing that appears to have been driven by specific events.
The researchers say that during the U.S. government shutdown in October 2025, the threat actor showed increased interest in scanning entities across North, Central and South America (Brazil, Canada, Dominican Republic, Guatemala, Honduras, Jamaica, Mexico, Panama, and Trinidad and Tobago).
Significant reconnaissance activity was discovered against “at least 200 IP addresses hosting Government of Honduras infrastructure” just 30 days before the national election, as both candidates indicated willingness to restore diplomatic ties with Taiwan.
Unit 42 assesses that the threat group compromised the following entities:
- Brazil’s Ministry of Mines and Energy
- the network of a Bolivian entity associated with mining
- two of Mexico’s ministries
- a government infrastructure in Panama
- an IP address that geolocates to a Venezolana de Industria Tecnológica facility
- compromised government entities in Cyprus, Czechia, Germany, Greece, Italy, Poland, Portugal, and Serbia
- an Indonesian airline
- multiple Malaysian government departments and ministries
- a Mongolian law enforcement entity
- a major supplier in Taiwan’s power equipment industry
- a Thai government department (likely for economic and international trade information)
- critical infrastructure entities in the Democratic Republic of the Congo, Djibouti, Ethiopia, Namibia, Niger, Nigeria, and Zambia
Unit 42 also believes that TGR-STA-1030/UNC6619 also tried to connect over SSH to infrastructure associated with Australia’s Treasury Department, Afghanistan’s Ministry of Finance, and Nepal’s Office of the Prime Minister and Council of Ministers.
Apart from these compromises, the researchers found evidence indicating reconnaissance activity and breach attempts targeting organizations in other countries.
They say that the actor scanned infrastructure connected to the Czech government (Army, Police, Parliament, Ministries of Interior, Finance, Foreign Affairs, and the president’s website).
The threat group also tried to connect to the European Union infrastructure by targeting more than 600 IP hosting *.europa.eu domains. In July 2025, the group focused on Germany and initiated connections to more than 490 IP addresses that hosted government systems.
Shadow Campaigns attack chain
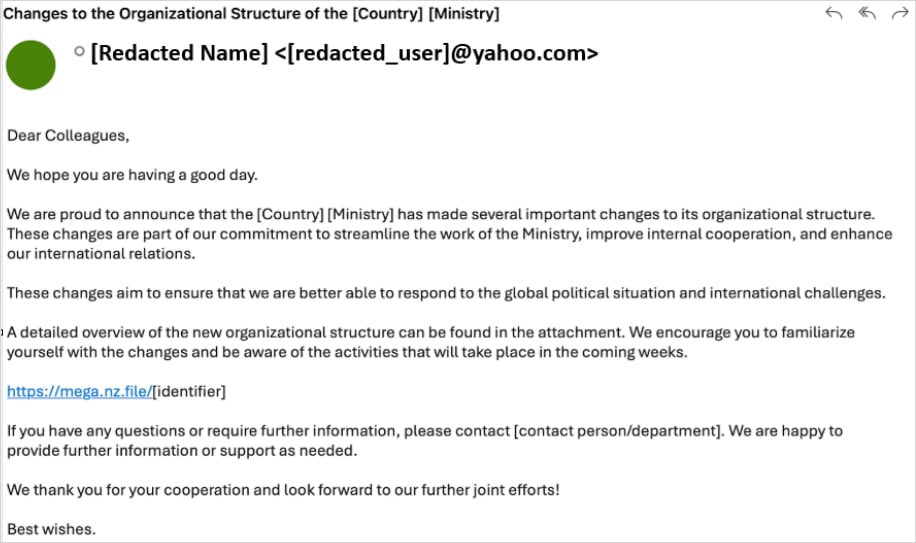
Early operations relied on highly tailored phishing emails sent to government officials, with lures commonly referencing internal ministry reorganization efforts.
The emails embedded links to malicious archives with localized naming hosted on the Mega.nz storage service. The compressed files contained a malware loader called Diaoyu and a zero-byte PNG file named pic1.png.
Source: Unit 42
Unit 42 researcher found that the Diaoyu loader would fetch Cobalt Strike payloads and the VShell framework for command-and-control (C2) under certain conditions that equate to analysis evasion checks.
“Beyond the hardware requirement of a horizontal screen resolution greater than or equal to 1440, the sample performs an environmental dependency check for a specific file (pic1.png) in its execution directory,” the researchers say.
They explain that the zero-byte image acts as a file-based integrity check. In its absence, the malware terminates before inspecting the compromised host.
To evade detection, the loader looks for running processes from the following security products: Kaspersky, Avira, Bitdefender, Sentinel One, and Norton (Symantec).
Apart from phishing, TGR-STA-1030/UNC6619 also exploited at least 15 known vulnerabilities to achieve initial access. Unit 42 found that the threat actor leveraged security issues in SAP Solution Manager, Microsoft Exchange Server, D-Link, and Microsoft Windows.
New Linux rootkit
TGR-STA-1030/UNC6619’s toolkit used for Shadow Campaigns activity is extensive and includes webshells such as Behinder, Godzilla, and Neo-reGeorg, as well as network tunneling tools such as GO Simple Tunnel (GOST), Fast Reverse Proxy Server (FRPS), and IOX.
However, researchers also discovered a custom Linux kernel eBPF rootkit called ‘ShadowGuard’ that they believe to be unique to the TGR-STA-1030/UNC6619 threat actor.
“eBPF backdoors are notoriously difficult to detect because they operate entirely within the highly trusted kernel space,” the researchers explain.
“This allows them to manipulate core system functions and audit logs before security tools or system monitoring applications can see the true data.”
ShadowGuard conceals malicious process information at the kernel level, hides up to 32 PIDs from standard Linux monitoring tools using syscall interception. It can also hide from manual inspection files and directories named swsecret.
Additionally, the malware features a mechanism that lets its operator define processes that should remain visible.
The infrastructure used in Shadow Campaigns relies on victim-facing servers with legitimate VPS providers in the U.S., Singapore, and the UK, as well as relay servers for traffic obfuscation, and residential proxies or Tor for proxying.
The researchers noticed the use of C2 domains that would appear familiar to the target, such as the use of .gouv top-level extension for French-speaking countries or the dog3rj[.]tech domain in attacks in the European space.
“It’s possible that the domain name could be a reference to ‘DOGE Jr,’ which has several meanings in a Western context, such as the U.S. Department of Government Efficiency or the name of a cryptocurrency,” the researchers explain.
According to Unit 42, TGR-STA-1030/UNC6619 represents an operationally mature espionage actor who prioritizes strategic, economic, and political intelligence and has already impacted dozens of governments worldwide.
Unit 42’s report includes indicators of compromise (IoCs) at the bottom of the report to help defenders detect and block these attacks.



