In 2024, the Cybersecurity Infrastructure and Security Agency (CISA) identified the need to develop a series of Skilling Continuation Labs to help the federal workforce improve operational cybersecurity in vulnerability management, defense architecture, and incident detection and response. The effort would support the Federal Civilian Executive Branch (FCEB) Operational Cybersecurity Alignment (FOCAL) Plan and additionally provide cyber operators with an environment where they can perform rehearsals with security tools, techniques, and configurations in accordance with CISA guidance, best practices, and publicly available toolsets.
This post details how the SEI Cyber Mission Readiness Team (CMR), in partnership with CISA, developed a series of Skilling Continuation Labs (SCLs) to provide current, relevant, and unique hands-on immersive training to upskill the federal cybersecurity workforce.
Upskilling the Federal Workforce
Federal cybersecurity professionals face a unique set of threats, risks, requirements, and regulations. To address this need, the SEI leveraged its experience with cybersecurity best practices, federal government guidance, and workforce development to deliver engaging, specialized training for federal cybersecurity professionals.
CISA hosts the Federal Cyber Defense Skilling Academy to provide the federal workforce with basic knowledge in key areas of cybersecurity such as incident response, vulnerability analysis, and defensive cybersecurity. Each pathway offers additional training to current federal IT and cybersecurity professionals but also provides avenues for non-IT professionals to break into the federal cybersecurity workforce. With this latest effort, SEI researchers wanted to provide the next level of hands-on immersive training to upskill academy graduates as they continue their transition into more advanced cybersecurity positions.
Learning Through Immersive Strategies
Immersive training provides an engaging and relatable experience for users to attain and practice applying new lesson concepts. Unlike traditional classroom and passive education models (e.g., lectures or autonomous video), immersive scenario-based content provides an environment where learners have a familiar context to better acquire knowledge and skills.
Strengthening and increasing the skillsets of cyber operators is key for workforce capacity building. As indicated in the SEI fact sheet, Approach to Skilling the Cyber Workforce, deliberate practice and comprehension validation through immersive, hands-on content is an effective means for building critical capabilities. This rehearsal for real-world operations and problem-solving allows defenders to improve skillsets and strengthens overall mission readiness.
Acquire, Apply, Affirm: The Catalyst for Skilling Continuation Labs
Where the military training model has coined the phrase crawl, walk, run, that approach doesn’t lend itself to upskilling those who already have foundational, novice-level skills (i.e., already walking). The SEI developed a broader upskilling philosophy of acquire, apply, affirm, a progression designed for professionals who already possess foundational skills and desire structured opportunities to improve those skills or to learn new ones. Our research team wanted to develop topic-focused, hands-on, guided labs with assessments to take users through the phases of acquiring, applying, and affirming the lesson’s skills.
CISA initially highlighted skills gap areas such as malware outbreaks, DNS security solutions and strategies, proactive defensive strategies, and basic security practices, with further topics identified throughout the project. Rather than simply reteach commonly addressed cybersecurity basics, each SCL focused on emerging threats, relevant/recent federal guidance, and cybersecurity trends tied directly to FOCAL Plan goals. Each SEI-developed skilling continuation lab is “created for cyber professionals with some IT/cyber experience who fall into the upper-beginner to lower-intermediate cyber skill range … these labs will provide a continuation of skills for the cyber professional.”
During the year-long development cycle, the SEI built 19 skilling continuation labs based on topics selected in collaboration with our CISA mission partners. A quick look at three of the skilling continuation labs follows:
- DNS and Name-based Security Solution and Fast Flux Attacks and Defensive Measures – These labs reviewed DNS basics while also introducing the concept of DNS sink holing, blocklist/allowlists, and highlighting how DNS can be used to circumvent traditional blocking methods in fast flux attacks such as IP-based firewall rules.
- Network Segmentation with ICS/HMI and Introduction to SCADA Using Modbus and BACnet – This set of labs introduces the learner to industrial controls systems, their traffic types, and how to implement network segmentation and access control best practices.
- XZ Utils: A Case Study of Supply Chain Trust – This set of labs provided learners a deep dive on the 2024 XZ Utils vulnerability while introducing the concept of Software Bill of Materials (SBOMs) to review open-source software for vulnerabilities and enhance the safety of software supply chains.
In addition to the three labs detailed above, the list of labs, which are published on CISA’s Practice Area, and accessible to all federal civilians and Department of War (DoW) personnel, includes the following:
- Automated Defenses
- Detection Rules in Logging Made Easy
- Fast Flux Attacks and Defensive Measures
- Hardening Kubernetes: Pod Security
- Incident Response with Velociraptor
- Introduction to SCADA Using Modbus and BACnet
- Living Off the Land Attacks
- Log Managements with Logging Made Easy
- Phishing Mitigation with MFA
- Secure Programming
- Secure Programming with Rust
- Secure Programming: Dependency Supply Chain Attacks
- Weaponized Archive Files: Extract at Your Own Risk
- Weaponized .svg Files: The Hidden Threat in Vector Graphics
- Web Application Penetration Testing with Brute Force Attacks
- Web Application Penetration Testing with Cross Site Scripting
Additional artifacts are published to CISA’s prescup-challenges/skilling-continuation-labs GitHub repository.
The SCL also included and promoted CISA tools like Logging Made Easy and Protective Domain Name System (DNS) Resolver, introduced proactive defensive measures such as using Endpoint Detection and Response simulation tools to detect ransomware, and provided users with environments to witness the effects of vulnerability exploitation, web application attacks, phishing attacks, and analyze weaponized file types.
What Makes the SCL Unique
The figure below illustrates the focus of SCLs on recent trends, threats and advisories, CISA-promoted tools, and the latest federal guidance.

Figure 1: Example of a lab introduction highlighting relevant CISA guidance and resources
Tied to the FOCAL Plan and NICE Workforce Framework for Cybersecurity (NICE Framework), each lab provides standalone and strategically aligned training in a realistic virtual network environment that simulates real-world networks and provides access to live operating systems and tools. The adherence to open-source tools and technologies means that others can replicate the strategies outlined within each lab with zero barriers and at no cost.
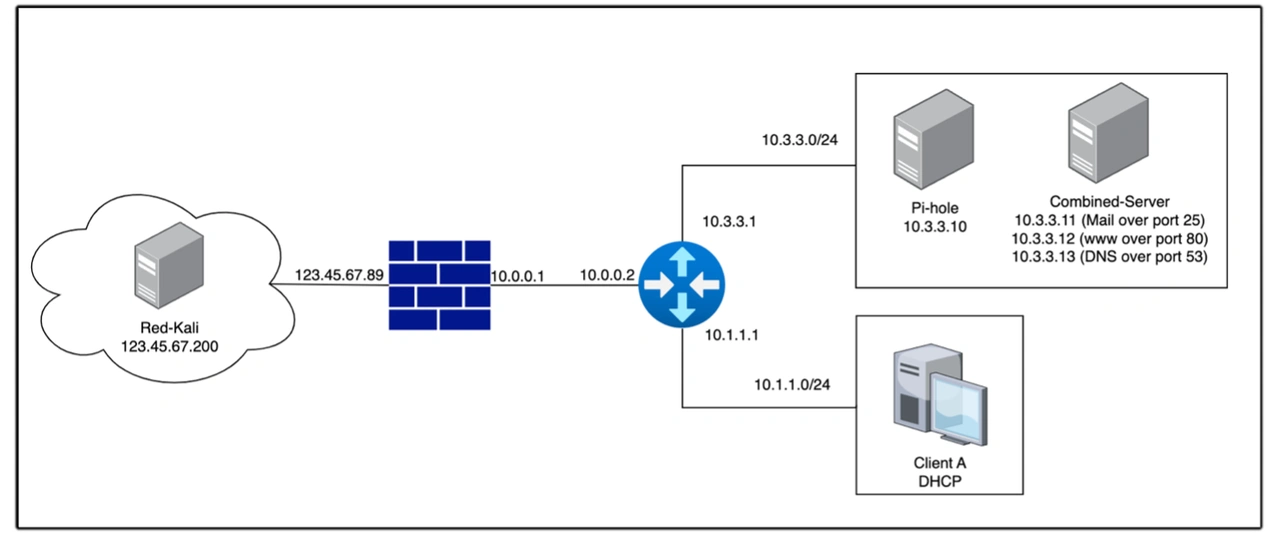
Figure 2: Example network diagram showing internal and external systems
The Skilling Continuation Labs differ from traditional virtualized teaching labs in the way they assess and challenge the learner. Each lab includes a Skills Hub as an authoritative server to track and assess the learner’s progress, provide in-game files and artifacts, and insert randomness into the environment. Instead of simply providing step-by-step tasks or asking questions, the Skills Hub affords developers the ability to query the state of the environment to gauge progress and the successful completion of lab tasks through Python-based grading scripts. The Skills Hub tracks and continually reports the current state of the lab back to the learner through an in-lab webpage.

Figure 3: Example: how the Skills Hub tracks and displays a learner’s progress
Local scripts allow developers to dynamically generate activities, network traffic, and generate files for analysis. For example, filenames, IP addresses, usernames and passwords, and more can be randomized to create entropy within the environment so that no two instances are completely identical. The dynamic nature adds replayability to the training.
Additionally, as shown in Figure 4, many of the labs include a mini-challenge that requires learners to apply the skills learned in the lab to a new problem with minimal guidance, allowing them to affirm their readiness and understanding of the topic at hand.

Figure 4: Example mini-challenge task and desired outcome
Future Work in Developing Training for the Federal Cybersecurity Workforce
The SEI’s Cyber Mission Readiness team continually strives to improve its immersive training development and delivery processes. After every project, developers discuss what improvements should be made to support future projects. Following our work on the SCL project, the SEI Cyber Mission Readiness team recommended the following improvements:
• Skills Pathways. The CMR team is currently in the process of adding skills pathways to the SEI’s Crucible platform to support roadmaps of content and increase a learner’s skill level in specific areas of cybersecurity or in certain cybersecurity roles. Adding skills pathways would walk learners through a progression of items of increasing difficulty, from guided lab walkthroughs to unguided challenges, allowing them to advance towards skills mastery.
• Bookmarking Session Status. Currently, a learner must complete a lab in a single session. While using lab phases allows learners to tackle tasks in segments, learners must restart the lab and repeat work they had previously done if their work did not complete the entire session. With additional development time, labs that require sequential phases could be scripted to stage the environment to the final state of the highest phase completed by the learner. Labs with sequential or isolated phases would store a learner’s progress so they would not need to repeat previously completed assessment items.
• Support Chat Agent. Tools for on-demand learner-initiated support and guidance could help learners when they are stuck. Leveraging logs and large language models (LLMs), the CRM directorate could create a chat agent capable of answering user questions and providing guidance and hints.
• Self-Configured Environment. An environment that learners can configure for performing cyber skills training would allow the learner to select from a list of skills to practice, while the environment that supports those skills is deployed automatically. Skills-based injects and activities could be applied to the environment, and supporting scenario documentation could be generated with LLM assistance.

