Facing an ever-evolving and increasingly sophisticated cybersecurity landscape, organizations have a pressing need to gain greater visibility of and insights into their network traffic. Most threats are delivered over encrypted channels, increasing the need to inspect encrypted traffic traversing the network to look for possible obscured threats.
In Cisco Secure Firewall version 10.0, our most recent software release, we’ve delivered four compelling new features to help customers quickly and efficiently assess and act on information in their network traffic. You can test drive these capabilities today with Secure Firewall Test Drive, an instructor led course that will guide you through the Secure Firewall and its powerful roles in cybersecurity for your organization.
Simplified decryption
The best way to gain visibility into encrypted traffic is to decrypt it. The new simplified decryption experience in Cisco Secure Firewall version 10.0 simplifies the steps required to enable and manage encryption. Instead of a traditional rules-based design, Easy Decrypt allows fast creation of inbound and outbound decryption policies by targeting internal servers via any type of network object.
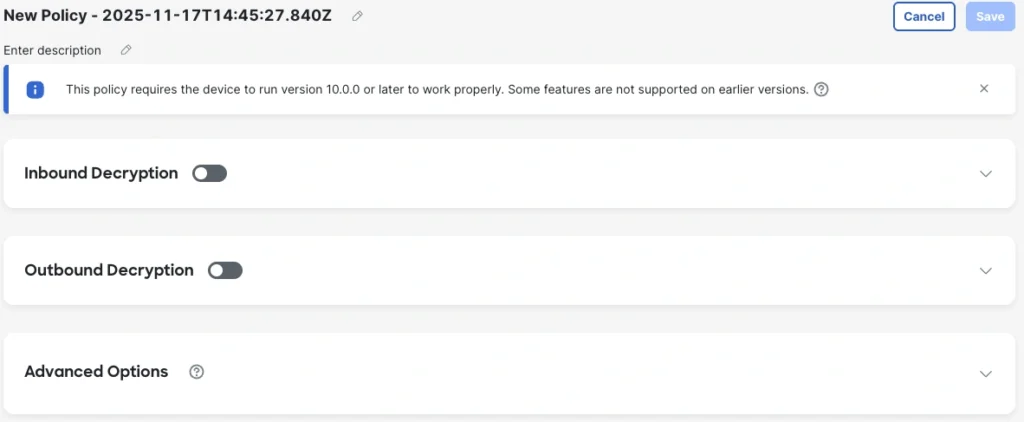

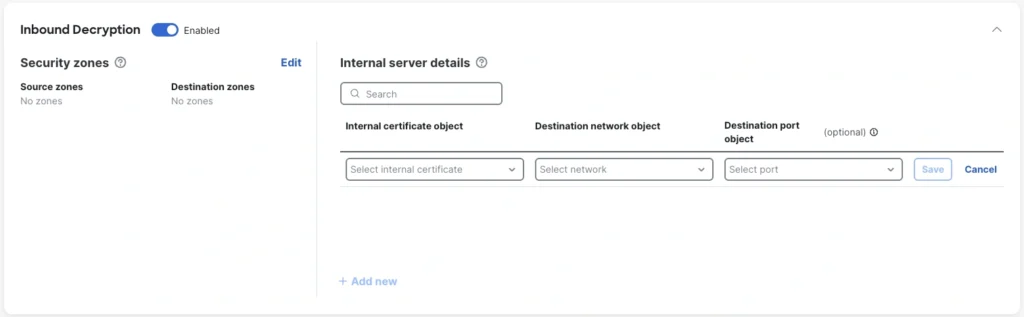

Additionally, certificates are individually selectable for each server. The public-facing certificates can be serviced by LetsEncrypt, significantly reducing certificate maintenance overheads. Outbound decryption certificate management can now be managed right from the decryption policy page, making for an easier workflow when building out policies.
All object types supported for decryption policies include key attributes such as fully qualified domain name (FQDN), URL, network and network groups and ranges, source group tags, dynamic objects, and more.
To ease selective decryption as needed, the Cisco-provided AppID bypass list allows excluding entries from this list for decryption. The previous release of Cisco Secure Firewall introduced Intelligent Decryption Bypass, further easing decision making around which traffic to decrypt by assessing low-risk traffic that is likely safe to bypass decryption processes. It determines what traffic is low risk by combining data from Talos reputation scores and the client threat confidence score presented by the Encrypted Visibility Engine (EVE).
Lastly, all new rules are automatically enabled for comprehensive logging to provide better visibility into rules’ usage and any potential considerations within the network.
QUIC decryption
Quick UDP Internet Connections (QUIC) is a natively encrypted secure protocol designed to increase the flexibility and performance of web applications while also bolstering security. However, it is also more difficult to gain visibility into this traffic, as the transport technology is different from traditional TCP-encrypted traffic. QUIC instead relies upon User Datagram Protocol (UDP) transport and directly implements TLS 1.3 into the session handshake, allowing encryption of handshake messages after the first packet. Whereas TCP+TLS encryption left handshake messages transparent to inspection, almost all handshake data after the first packet is hidden with QUIC. Even the Server Name Indicator (SNI), which specifies the server the client is communicating with, can be encrypted by implementing Encrypted Client Hello (ECH) alongside QUIC.
Several obfuscations within QUIC make it difficult to trace or follow a full QUIC session, such as:
- Sequence numbering in the header is encrypted
- No TCP metadata exists, such as for SYN, ACK, FIN, RST messages
- Multiplexed streams are hidden inside the encryption
- The connection can be migrated across IP addresses without transport header indication
The express purpose of QUIC is to leave only the essential information a router or similar device requires to transmit and forward packets, but this goal runs contrary to the security and accountability goals of many organizations.
QUIC adoption is on the rise among global web traffic, increasing from about 7% usage in 2020 to around 45% usage in 2025. About a third of all web services and over 80% of Google services are now QUIC-first (that is, services where QUIC is offered before TCP+TLS).
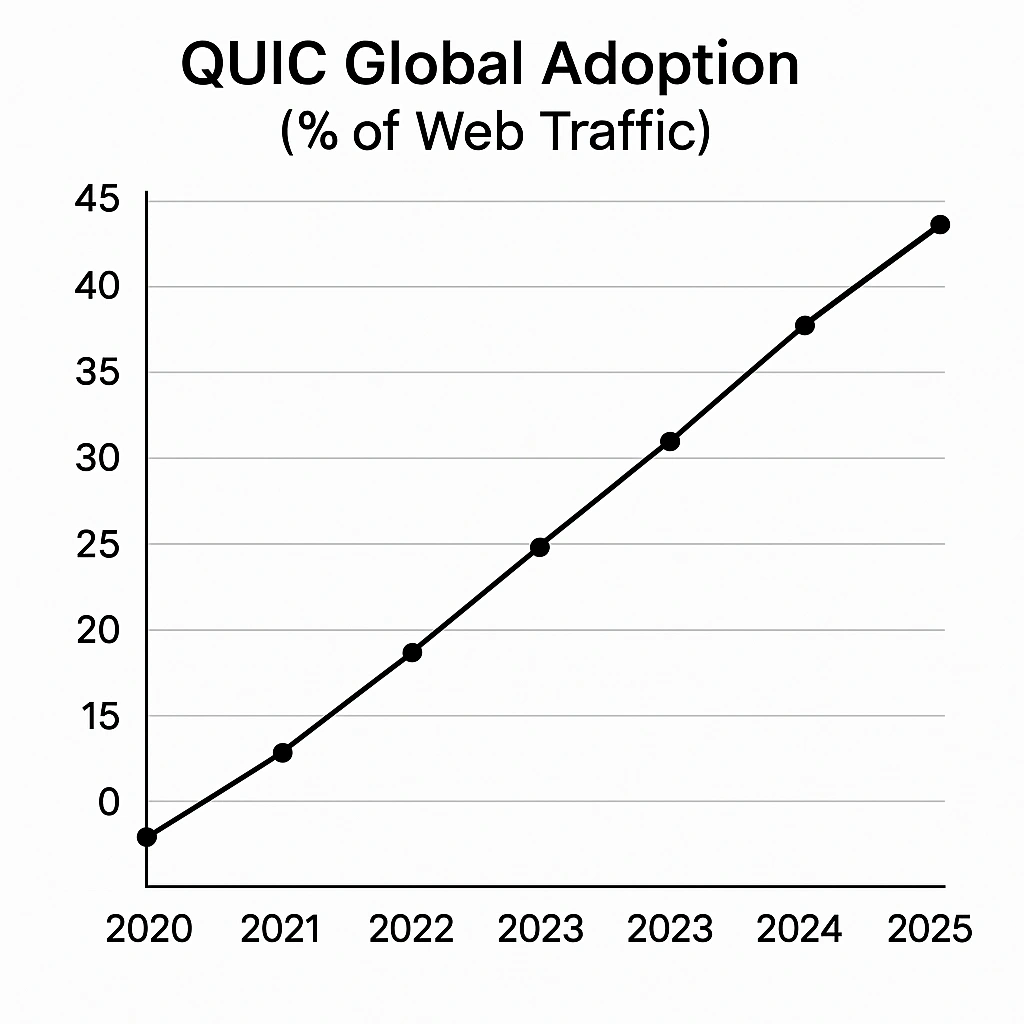

Considering this rising adoption and the need for greater visibility and control where the QUIC protocol is in use, decryption policies in Cisco Secure Firewall version 10.0 have been enhanced to allow decryption and inspection upon QUIC traffic to ensure visibility is maintained while taking advantage of the improvements offered by this protocol.
In environments and use cases where decryption of QUIC traffic isn’t possible, the Encrypted Visibility Engine (EVE) provides highly accurate fingerprinting of QUIC traffic that uniquely characterizes and analyzes QUIC-encrypted sessions to assess post-exploit beaconing and similar suspicious traffic. This compelling capability helps ensure that all organizations can gain insight and protections for QUIC traffic as the usage of this protocol increases.
Shadow traffic reporting
Some techniques offered by privacy technologies cause a loss of visibility within organizational networks. This collection of new “Loss of Visibility” reports focuses on these cases, offering statistical and detailed reports to help identify traffic where security analysis is incomplete due to obfuscations between the source and destination.
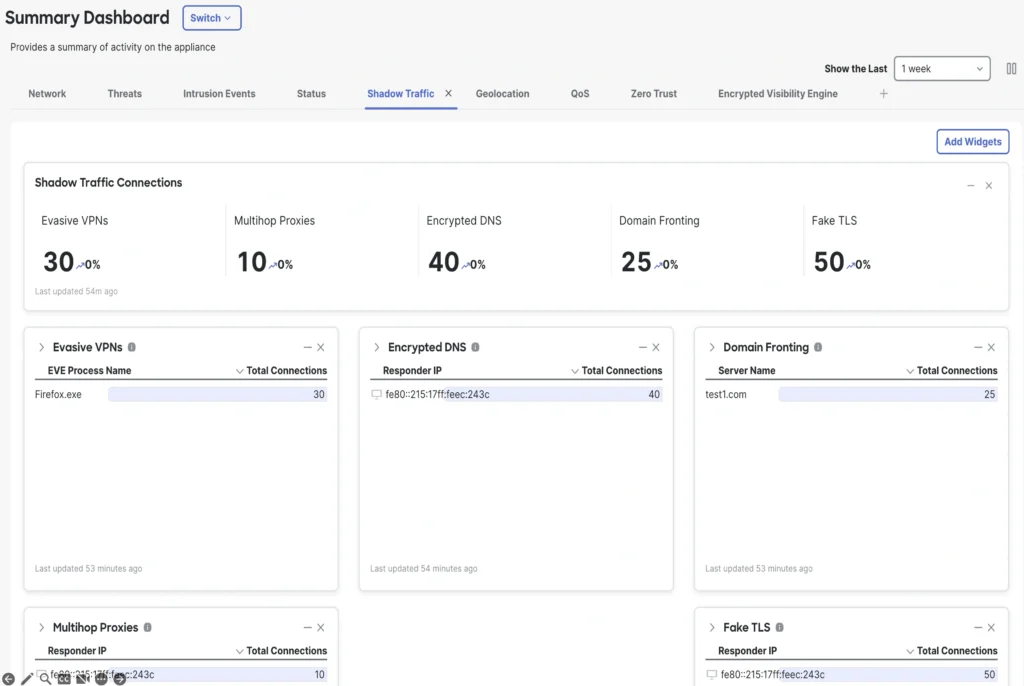

Included “Loss of Visibility” reports
Multihop proxies: Traffic passing from a client to a proxy that in turn passes to one or more proxies becomes difficult to trace to origin and may indicate an attempt to hide attack attempts.
Encrypted DNS: If domain name lookup information is not available, then policies restricting certain domain names do not take effect as expected.
Fake TLS: Some traffic contains TLS handshakes, headers, or other implementations that indicate TLS encryption is employed while not actually conforming to the protocol, instead providing a route for malware attacks, command and control beaconing, or tunneling non-encrypted traffic.
Evasive VPN: Some VPN services intentionally conceal signals indicating their use through means such as traffic masking or obfuscating the protocols used for the traffic. When evasive VPNs are detected, the application making the evasive connections is identified in the Shadow Traffic view, allowing for simple policy creation to block that process.
Domain fronting: Some connections will advertise widely trusted front domains in the SNI, then use a different HTTP host header inside the encrypted connection to direct traffic to a different backend service on the same provider. This can cause rules that allow widely trusted domains to have unintended side effects, allowing traffic that is not desirable. These domain-fronting URLs are displayed in the Shadow Traffic view to highlight where policy decisions may need to be made.
Additionally, it’s now easier to modify configurations to disallow these technologies where desired.
Advanced logging
To enhance the already robust set of information available for logged connections within Cisco Secure Firewall and Cisco Secure Network Analytics, a new log type has been created and made searchable. Characteristics logged include:
Application metadata: Identify suspicious applications or attempted misuses of known applications with exposure to the metadata pertaining to that application
Intelligent PCAPs: Detailed packet data to facilitate deep forensics of security events
Deeper insights on layer 5-7 connections: This focus on more detailed information about session, presentation, and application layer traffic provides more comprehensive visibility into application-level activities to investigate breaches even where network level traffic looks benign or trusted
HTTP, FTP, DNS, and connection logging: By detailing web, file transfer, domain lookup, and general connection data, greater context is available for closer investigations of security events
Weird logging: Capturing protocol deviations and unusual network behaviors alert security teams to traffic that may signal novel attacks or misconfigurations within applications and networks
Notice logging: Specifically, security-relevant events are grouped and surfaced to aid in threat hunting and analysis
This enhanced data helps network and security administrators understand more about the traffic in their organization’s network and make informed policy decisions and recommendations.
Splunk correlation with advanced logging
The deeper insights in advanced logging allow for Splunk correlations to existing Cisco Secure Firewall logs and events, as well as other network and security logs and data within organizational environments and monitored by the organization’s Splunk instance. These correlations offer opportunities to more quickly detect, triage, and create responses to security events by streamlining efforts to trace the event through the network and find additional signals to understand the event’s impact.
Take a hands-on look at Cisco Secure Firewall 10.0
Want to dive deeper into Cisco firewalls? Sign up for the Cisco Secure Firewall Test Drive, an instructor-led, 4-hour hands-on course where you’ll experience the Cisco firewall technology in action and learn about the latest security challenges and attacker techniques.
We’d love to hear what you think! Ask a question and stay connected with Cisco Security on social media.
Cisco Security Social Media

